Content:
- Introduction
- The Anatomy of an Insider Threat
- Identifying Potential Insider Threat
- Implementing Proactive Insider Threats
- The Impact of Insider Threat
- Preventing Insider Threat
- Detecting and Responding to Insider Threats
- Building a Security-Minded Culture
- The Role of Technology in Threat Prevention
- Responding to Insider Threat
- Insider Threat Case Study
- Partnerships and Collaboration
- Balancing Security and Productivity
- The Future of Insider Threat Mitigation
- Insider Threats and the Remote Work Paradigm
- Navigating the Legal and Regulatory Landscape
- Conclusion: Embracing a Proactive Approach
- FAQs:
Introduction
Insider threats pose a serious risk to businesses of all sizes. A disgruntled former employee with access to your network can steal valuable intellectual property and customer data, causing significant damage. In this guide, we’ll explore the nature of Insider Threat, the steps you can take to prevent them, and what to do if an incident occurs.
The Anatomy of an Insider Threat
Insider threats are security breaches that come from within your organization. They can involve current or former employees, contractors, or business partners. These individuals often have legitimate access to your networks, systems, and data. Consequently, they can exploit this access for personal gain or to harm your business. Insider threats can manifest in various ways, such as data theft, sabotage, and unauthorized access to sensitive information.
For example, consider a real-life incident involving a disgruntled former tech startup employee. This employee retained access to the company’s network and stole intellectual property. However, The stolen data included secret codes and customer information, which they used at a competitor.
Such incidents can be devastating. They compromise your data and give your competitors an unfair advantage.
Identifying Potential Insider Threat
Recognizing the warning signs of an insider threat is crucial for proactive risk management. Therefore, it’s essential to be aware of some common indicators, such as:
- Disgruntled or dissatisfied employees
- Employees facing financial difficulties or personal problems
- Sudden changes in behaviour or work patterns
- Attempts to access sensitive information or systems outside of regular job duties
By staying vigilant and addressing these red flags promptly, we can take steps to mitigate the risks before they escalate.
Implementing Proactive Insider Threats
To effectively mitigate insider threats, businesses should adopt a comprehensive security strategy that includes the following key elements:
Access Controls:
Implement robust access controls, such as multi-factor authentication. This helps limit employee access to only the systems and data they need to perform their jobs.
Ongoing Monitoring:
Furthermore, user activity and system logs should be regularly monitored. Similarly, This helps detect and respond to suspicious behaviour promptly.
Employee Education:
Additionally, educate employees on the importance of information security. Also, guide them on the signs of potential insider threats and their role in reporting suspicious activities.
Incident Response Plan:
Moreover, a comprehensive incident response plan should be developed to guide the organization’s actions in case of a suspected or confirmed insider threat incident.
The Impact of Insider Threat
Insider threats can have severe and widespread effects on businesses. The theft of intellectual property can cause significant financial losses and reduce competitiveness. Eventually, Unauthorized disclosure of sensitive data can lead to fines, legal issues, and severe damage to our reputation.
Additionally, insider attacks can disrupt operations, lower productivity, and break customer trust. Recovering from such incidents takes much time and money, making the financial and reputational damage even worse.
Preventing Insider Threat
To reduce the risk of insider threats, it’s essential to establish a comprehensive security strategy that covers both technical and human-related aspects. So, Here are a few key steps to consider:
Implement Strong Access Controls:
First and foremost, carefully manage user access to your network, systems, and data. Then, limit privileged access, regularly review and revoke permissions, and implement multi-factor authentication.
Conduct Thorough Onboarding and Offboarding:
Additionally, ensure that your onboarding process includes security training and transparent policies. When employees leave, promptly revoke all access and monitor for suspicious activity.
Foster a Culture of Responsibility:
Moreover, employees should be encouraged to be vigilant and report suspicious behaviour or potential security breaches. Meanwhile, Promote a culture of security awareness and accountability.
Detecting and Responding to Insider Threats
Even with strong preventive measures, it’s crucial to be ready to detect and respond to insider threats quickly. Here are some steps to take:
| Implement Monitoring and Alerting | First, security tools should be used to keep an eye on user activity. Detect anomalies and set up alerts. This helps you catch and investigate potential insider threats early. |
| Develop an Incident Response Plan | Next, have a clear plan for handling security incidents. First, security tools should be used to keep an eye on user activity. Detect anomalies and set up alerts. This helps you catch and investigate potential insider threats early. |
| Collaborate with Authorities | Lastly, work with law enforcement and legal authorities if an insider threat occurs. As a result, this helps investigate the incident and take legal action if needed. Holding the perpetrator accountable can reduce the impact on your business. |
Building a Security-Minded Culture
Building a strong security-minded culture in your organization is key to reducing insider threats. Here’s how to do it:
| Employee Engagement | First, involve employees in security awareness training. Encourage them to openly discuss security concerns and recognize their role in keeping the environment secure. |
| Policies and Procedures | Next, create clear security policies, procedures, and guidelines. Also regularly review these to make sure that they are up-to-date. However, make sure everyone knows the expectations and the consequences of not following them. |
| Leadership Commitment | Lastly, senior leadership should actively support and show a strong commitment to information security. When leaders set a good example, it sets the tone for the entire organization. |
The Role of Technology in Threat Prevention
Privileged Access Management (PAM):
Start by using strong PAM solutions. These tools monitor and control who has access to critical systems and data. Therefore, They help stop unauthorized access and spot suspicious activity early.
User and Entity Behaviour Analytics (UBA):
Next, UBA tools are used to track normal user behaviour. These tools set a baseline and flag any unusual activity that might signal a threat. However, this helps you to identify and respond to threats quickly.
Data Loss Prevention (DLP):
Finally, deploy DLP solutions to keep an eye on sensitive data. These tools control how data flows inside and outside your organization, spotting and stopping unauthorized data transfers.
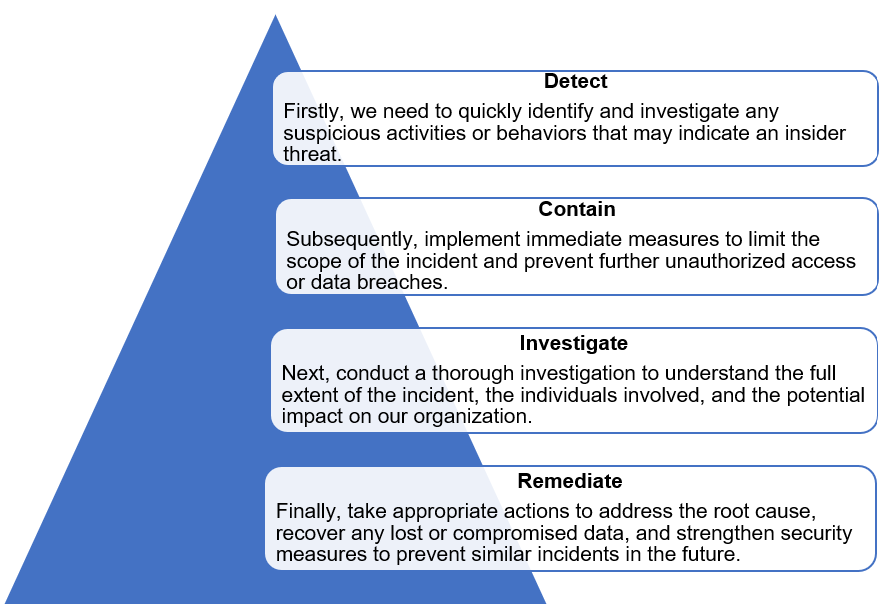
Responding to Insider Threat
Even with strong measures in place, insider threats might still occur. That’s why it’s essential to have a clear incident response plan. This plan should outline how to reduce the impact and limit any further damage.
Insider Threat Case Study
The Disgruntled Employee:
Consider the case of a disgruntled ex-employee from a tech startup. This individual retained access to the company’s network, which they used to steal valuable intellectual property, such as proprietary code and customer data. Subsequently, they used this stolen information to gain an advantage over a competitor.
The consequences were severe. The competitor undercut our pricing and attracted vital customers, leading to significant financial losses. Moreover, our reputation suffered greatly, and we had to allocate substantial resources to investigate the breach and recover the stolen data.
This situation highlights the need for robust security measures. Therefore, we must implement strict access controls, continuously monitor activity, and establish comprehensive termination procedures to mitigate the risk of insider threats.
Check this below video: how insider threat works in real life
The Sony Pictures Hack :
In 2014, Sony Pictures encountered a major insider threat when hackers, known as the Guardians of Peace, breached its network. They stole a massive amount of sensitive data, including emails, employee records, and unreleased films. Believed to be connected to North Korea, these hackers released the stolen information online, substantially damaging Sony’s reputation and operations.
This high-profile incident highlights the urgent need for robust security measures. By examining the Sony Pictures case, businesses can understand the severe impact of insider threats. This awareness can drive them to take proactive steps to safeguard their operations.
Partnerships and Collaboration
Addressing insider threats takes teamwork from everyone inside and outside your organization. By building strong partnerships and clear communication, you can tap into a broad range of expertise and resources to boost your security.
| Trusted Advisors | Cross-Functional Collaboration | Information Sharing |
| Firstly, connect with cybersecurity experts, industry groups, and government agencies. They can update you on the latest threats and best practices for dealing with insider threats. Also, We can help you find the right experts and resources. | Next, encourage teamwork between departments like IT, HR, and legal. Therefore, this ensures a coordinated approach to managing threats. Combining different perspectives and skills can create a robust and unified strategy. | Finally, get involved in information-sharing initiatives. Then, Stay updated on new threats and share insights with other organizations. By exchanging knowledge, everyone benefits and strengthens their defences together. |
Balancing Security and Productivity
Implementing strong security measures to guard against insider threats can sometimes feel like it slows down productivity and collaboration. So, finding a balance between security and efficiency is essential to keep your workforce engaged and effective.
| Streamlined Processes | First, we need to create security controls that are easy to use and fit smoothly into your daily routines. In the same way, we minimize disruptions to your work and keep things running smoothly. |
| Employee Empowerment | Next, we want to empower you to participate actively in our security efforts. Therefore, we’ll provide the training, resources, and tools you need to help protect our organization’s assets. |
| Transparent Communication | Lastly, we’ll communicate openly and clearly about why security measures are important, the reasons behind them, and how they benefit the entire organization. In the same way, everyone will understand and support our security goals. |
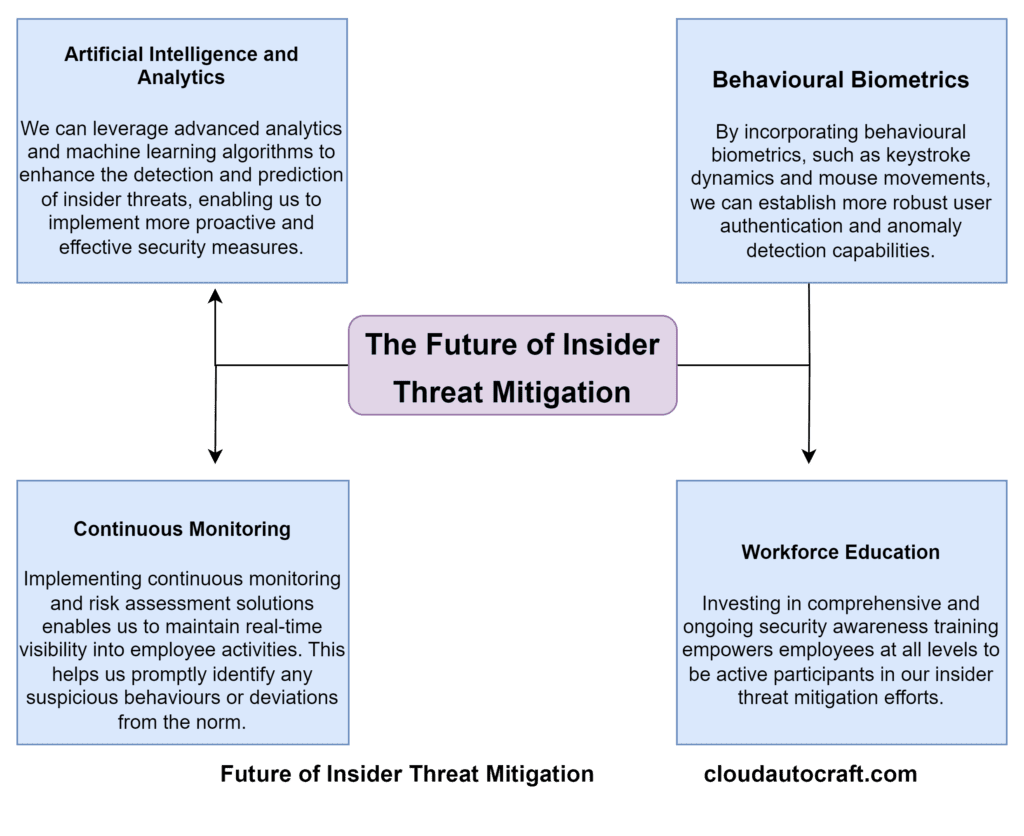
The Future of Insider Threat Mitigation
As technology advances and threats grow more complex, we must stay alert and adjust our threat mitigation strategies. Moreover, This will allow us to tackle future challenges effectively and strengthen our defences.
Insider Threats and the Remote Work Paradigm
The COVID-19 pandemic has significantly increased remote work, introducing new challenges for threat prevention. As many of you work from home, the traditional security perimeter has become blurred, making monitoring and controlling access to sensitive information more difficult.
To address this, we should implement additional security measures, such as multi-factor authentication, virtual private networks (VPNs), and endpoint detection and response (EDR) solutions. Moreover, regular training on best practices for remote work security is crucial. Finally, this ensures that everyone stays informed and protected.
Navigating the Legal and Regulatory Landscape
Addressing insider threats also means understanding the legal and regulatory rules that apply to your business. Depending on your industry and location, you might need to follow data privacy and security laws like the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA).
First, it’s crucial to ensure our threat prevention and response strategies comply with these regulations. Not following the rules can lead to expensive fines and damage to our reputation. Additionally, working with legal experts can help us handle the complexities of investigating and responding to incidents. However, This includes managing sensitive information properly and taking legal action against those responsible.
Conclusion: Embracing a Proactive Approach
Insider threats are a significant risk for businesses of all sizes. However, by taking a proactive and thorough approach to security, we can effectively manage these risks and protect our valuable assets.
To conclude, success depends on combining strong technical controls with a security-focused culture and teamwork across our organization. By staying alert, constantly improving our security measures, and involving everyone in the solution, we can create a solid defence against threats and secure the future of our business.
Click here to Read more about Phishing Attacks: How to Secure Banks – 2024 && Ransomware Threat: How to Secure Your Business – 2024
FAQs:
How do I determine if my business is vulnerable to insider threats?
Answer: First, assess employee access levels and behaviours. Next, regularly audit systems and conduct risk assessments to spot any vulnerabilities.
What are the most effective strategies for preventing insider threats?
Answer:Implement strong access controls, such as multi-factor authentication and least privilege access. Also, provide ongoing security training for employees and monitor user activity for suspicious behaviour.
How can I create a security-conscious culture within my organization?
Answer: To build awareness, start with regular communication and training. Encourage reporting of security concerns. Also, it incentivizes security-conscious behaviour and promotes accountability.
What are the legal implications of insider threats, and how can I ensure compliance?
Answer: Stay updated on relevant regulations like GDPR and HIPAA. Consult legal experts to ensure compliance. Also, integrate compliance measures into your security protocols and response plans.
Originally posted 2024-06-06 12:22:58.


6 thoughts on “Insider Threat: How to Secure Your Business”