For example, suppose your company operates in a highly regulated industry with strict security and compliance requirements. How would you design and implement a robust, secure AWS Cloud Infrastructure? This includes identity and access management (IAM), data encryption, network security, and compliance auditing. In this guide, I will walk you through these crucial areas.
Content:
- Apply IAM Policy To Secure AWS Cloud Infrastructure
- Data Encryption for Secure AWS Cloud Infrastructure
- Compliance Auditing for Secure AWS Cloud Infrastructure
- Network Security of Secure AWS Cloud Infrastructure
- Threat Monitoring of Secure AWS Cloud Infrastructure
- Incident Response and Disaster Recovery
- Secure AWS Cloud Infrastructure: Regulatory Compliance
- Security Incident Response
- Security Awareness for Secure AWS Cloud Infrastructure
- Secure AWS Cloud Infrastructure & DevOps Practices
- Governance and Risk Management
- Conclusion
- FAQs:
- What are some common security risks associated with AWS cloud infrastructure?
- How can I prevent unauthorized access to my AWS cloud infrastructure?
- What steps should I take to ensure data privacy and encryption within my AWS infrastructure?
- What measures should I take to ensure compliance with regulatory requirements when using AWS?
Apply IAM Policy To Secure AWS Cloud Infrastructure
Implementing a well-structured Identity and Access Management (IAM) strategy is very much required for your AWS security. Start by defining precise permissions for users, groups, and roles, giving each only the minimum access needed for their tasks. Additionally, features like multi-factor authentication, password policies, and temporary credentials can be used to boost the security of user identities.
Make it a habit to review and audit your IAM settings regularly. Moreover, This ensures they align with your evolving security needs and comply with industry regulations.
Data Encryption for Secure AWS Cloud Infrastructure
Protecting sensitive data is crucial, especially in regulated industries where compliance matters. Fortunately, AWS provides various encryption options to keep your data safe at rest and in transit.
Enable server-side encryption for Amazon S3 buckets and Amazon Elastic Block Store (EBS) volumes to protect data at rest. Consequently, your data gets automatically encrypted.
For data in transit, use AWS PrivateLink or AWS Direct Connect to establish private, encrypted connections between your on-premises infrastructure and the cloud. In the same way, your data remains secure as it moves.
Additionally, consider integrating AWS Key Management Service (KMS) for extra security. KMS lets you create and manage your encryption keys, giving you centralized control over their creation, rotation, and usage. With customer-managed keys, KMS ensures your data stays protected.
Compliance Auditing for Secure AWS Cloud Infrastructure
AWS Config
To boost your AWS security, start by using AWS Config. This service continuously monitors and logs your Amazon web service resource configurations. Doing so helps you assess, audit, and ensure that your resources meet industry standards and best practices.
CloudTrail
Next, enable AWS CloudTrail to track user activity and API calls within your AWS environment. By doing this, CloudTrail provides a detailed audit trail. As a result, it becomes easier to monitor and investigate suspicious activities.
Security Hub
Moreover, use AWS Security Hub to maximize your security. This central tool helps you monitor security and compliance by collecting and prioritizing alerts from AWS services. It also integrates with third-party tools for comprehensive protection.
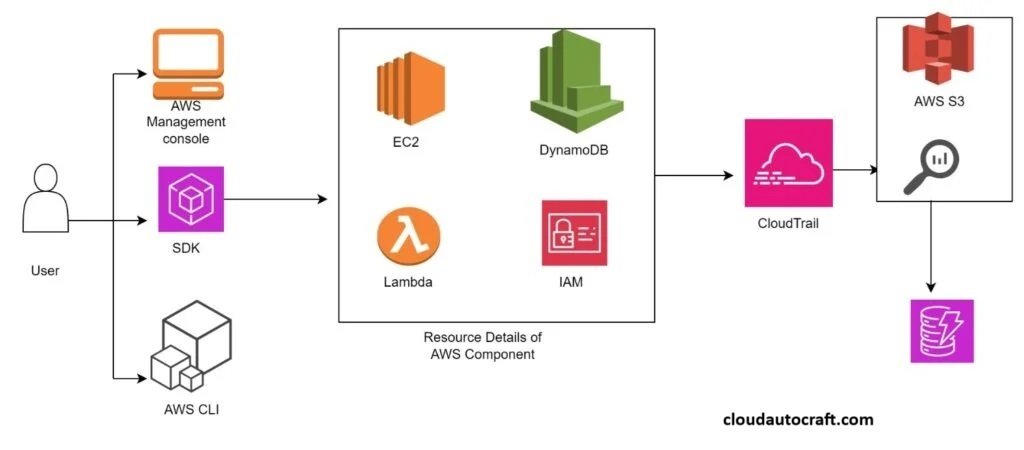
Architecture for compliance auditing and security
Network Security of Secure AWS Cloud Infrastructure
Upgrade Your Cloud Security with AWS VPC:
- Boost your cloud security with AWS VPC (Virtual Private Cloud) and its features. To start, create a private VPC with subnets, routes, and gateways to manage traffic. Next, use Security Groups as virtual firewalls to control access to IPs and ports.
- Additionally, deploy AWS Network Firewall to monitor traffic effectively. Hence, this helps you enforce security policies easily. Furthermore, AWS WAF can be integrated to protect web apps from common threats.
- Finally, explore AWS VPN or Direct Connect for secure connections between your on-premises infrastructure and the cloud.
By following these steps, you can significantly enhance the security of your cloud environment.
Threat Monitoring of Secure AWS Cloud Infrastructure
Proactive Threat Monitoring with AWS:
To stay ahead of security threats, let’s implement proactive threat monitoring. Start by using AWS GuardDuty. Eventually, this managed threat detection service monitors your AWS environment’s malicious activity and unauthorized behaviour.
Integrate AWS Security Hub with AWS Security Lake:
Additionally, consider integrating AWS Security Hub with AWS Security Lake. Security Lake is a data analytics service that centralizes and analyzes security data from various sources. Therefore, this integration helps you gain deeper insights, spot patterns, and respond to security incidents more effectively.

Continuously collect and analyse threat intelligence from diverse sources. Therefore, this updates you on the latest security threats, vulnerabilities, and attack methods targeting your industry.

Implement robust security monitoring and logging systems, like Amazon GuardDuty and AWS Security Hub. So, these tools help you quickly identify and respond to security issues.

Finally, build and regularly test your incident response plan. Therefore, this ensures your team is prepared to handle security incidents effectively. By swiftly containing, eradicating, and recovering from incidents, you minimize the impact on your business operations.
Incident Response and Disaster Recovery
| Centralized Logging and Monitoring | Incident Response Planning | Security Automation |
| Start by setting up a robust system for logging and monitoring. For instance, use tools like Amazon CloudWatch and AWS CloudTrail. These tools provide real-time insights into your AWS resources, which helps you identify security issues as they arise. As a result, you can take quick action to address potential threats effectively. | Next, having a solid incident response plan is crucial. Start by creating a detailed plan outlining the steps your team should take in case of a security breach or regulatory issue. Furthermore, make sure to test and update this plan regularly. Doing so ensures that it remains effective as new threats emerge. | Take advantage of AWS’s automated security tools. For example, Amazon GuardDuty, AWS Security Hub, and AWS Config Rules can handle much of the heavy lifting. These tools automatically detect, investigate, and address security issues. As a result, your team can respond more swiftly and efficiently to potential threats, providing you with greater peace of mind. |
Secure AWS Cloud Infrastructure: Regulatory Compliance
HIPAA Compliance: If your organization works in healthcare, following the Health Insurance Portability and Accountability Act (HIPAA) is essential. Luckily, AWS provides various tools to help you meet HIPAA requirements. These tools include data encryption, access controls, and audit logs to track user activities effectively.
PCI DSS Compliance: Compliance with the Payment Card Industry Data Security Standard (PCI DSS) is crucial when dealing with credit card transactions. Fortunately, AWS can assist you in setting up a PCI DSS-compliant system in the cloud. Specifically, they provide guidance and resources to ensure your setup meets the necessary standards.
GDPR Compliance: On the other hand, if your organization handles data from EU residents, you must comply with the General Data Protection Regulation (GDPR). This regulation protects personal information within the EU. Thankfully, AWS offers tools for GDPR compliance, such as data encryption, access controls, and features that respect individuals’ data rights.
Security Incident Response

Security Awareness for Secure AWS Cloud Infrastructure
Keeping your cloud infrastructure secure and compliant is an ongoing job. So, you need to regularly check and update your security setup, policies, and controls. In the same way, you can tackle new threats, follow new rules, and adjust to changing business needs.
Regular Vulnerability Assessments: Regularly checking for vulnerabilities is critical to finding and fixing security weaknesses in your AWS environment. Tools like AWS Security Hub, Amazon Inspector, and third-party scanners are used to do this. By monitoring potential issues with these tools, you can address them quickly and keep your environment secure.
Security Awareness and Training: Investing in training for your team is essential. So, educating employees on best practices, security policies, and how to report incidents is necessary. However, this helps them understand how to protect your cloud environment better.
Working Together for Security: Collaborate with your cloud provider, security partners, and industry peers. Moreover, this keeps you informed about the latest threats, best practices, and new solutions. Regularly update your security measures to keep up with evolving needs and technologies.
Secure AWS Cloud Infrastructure & DevOps Practices
Infrastructure as Code: Automate and secure your AWS resources with tools like AWS CloudFormation. Moreover, this lets you set up and manage your infrastructure quickly and safely.
Secure Code Repositories: Store your code in secure places like AWS CodeCommit. Ensure that access is valid for authorized people only. Also, set up processes for reviewing code and protecting branches. In addition, this helps keep your codebase secure.
Secure CI/CD Pipelines: Furthermore, Build secure CI/CD pipelines for continuous integration and deployment. Include security checks, vulnerability scans, and automatic security updates. Therefore, This ensures your code is always protected as it moves through the pipeline.
Governance and Risk Management
| Governance: | Start by setting clear security and compliance rules, roles, and responsibilities. Moreover, this ensures everyone knows their duties and that security measures are consistently applied across your AWS environment. |
| Risk Assessment: | Regularly assess the risks associated with your AWS setup. Think about potential threats and weaknesses and how these could impact your business. Finally, Use this information to prioritize security actions and make improvements. |
| Compliance Monitoring: | Furthermore, Continuously monitor your compliance status. Tools like AWS Config and AWS Security Hub can help you detect and address any deviations from your security and compliance standards. |
Conclusion
In conclusion, creating a solid security framework on AWS is crucial, especially for businesses in regulated industries. It may be complex, but it’s essential. By using AWS’s security services and sticking to best practices, you can build a cloud environment that’s secure, compliant, and resilient. Therefore, this helps protect your sensitive data and meets your organization’s strict security requirements.
Remember, security and compliance are ongoing tasks, not just one-time fixes. Keep monitoring and evaluating your security setup to stay ahead of new threats. Also, I need to be flexible with changing regulations to maintain continuous compliance.
Click here to read more about Best Practices for Cloud Migration: How to Achieve Success && Cost Optimization Strategies for AWS
FAQs:
What are some common security risks associated with AWS cloud infrastructure?
Answer: Some common security risks include misconfigured security settings, unauthorized access, data breaches, and lack of visibility into cloud environments.
How can I prevent unauthorized access to my AWS cloud infrastructure?
Answer: You can prevent unauthorized access by implementing strong authentication mechanisms, such as multi-factor authentication (MFA), regularly rotating access keys, and setting up strict access control policies.
What steps should I take to ensure data privacy and encryption within my AWS infrastructure?
Answer: To ensure data privacy and encryption, you should encrypt data at rest and in transit using services like AWS Key Management Service (KMS) and SSL/TLS encryption. Additionally, regularly audit and monitor access to sensitive data.
What measures should I take to ensure compliance with regulatory requirements when using AWS?
Answer: To stay compliant with regulatory requirements, audit your AWS environment against the relevant standards regularly. Implement logging and monitoring solutions to help with compliance reporting. Also, use AWS services like AWS Config and AWS Artifact to manage and document your compliance efforts effectively.
Originally posted 2024-04-27 06:48:49.


3 thoughts on “How to Secure AWS Cloud Infrastructure”