This document focuses on the serious problem of Unauthorized AWS Access. First, we’ll discuss the risks posed by former employees exploiting this security gap. Then, we’ll look at effective ways to reduce these risks. Finally, we’ll offer practical advice to ensure strong protection for your cloud setup.
Content:
- The Impact of Unauthorized AWS Access
- Understanding the Unauthorized AWS Access Threat
- The Role of Identity and Access Management (IAM)
- Key Mitigation Strategies of Unauthorized AWS Access
- Utilize AWS CloudTrail and CloudWatch
- Enable AWS Security Hub
- Implement Network Segmentation
- Real-World Example: A Case Study
- Leveraging AWS Security Best Practices
- The Power of Automation
- Unauthorized AWS Access: Employee Awareness Training
- Best Practice with Latest Updated
- Unauthorized AWS Access: Beyond Credentias
- The Role of Collaboration for Unauthorized AWS Access
- Regularly Review and Update Security Measures
- Conclusion
- FAQs:
- How do we ensure timely revocation of ex-employee access across AWS services?
- How do we balance security and efficiency in revoking access for departing employees?
- What steps detect and respond to ex-employees attempting Unauthorized AWS Access?
- How do we effectively communicate and enforce AWS security policies to employees?
The Impact of Unauthorized AWS Access
Imagine this: A former employee, upset and still having access to your AWS account, decides to cause trouble. They could change data, disrupt services, or even steal sensitive information. This isn’t just a hypothetical threat; it’s a real risk that needs urgent attention.
Understanding the Unauthorized AWS Access Threat
Unrevoked credentials are a significant security risk. So, they let unauthorized people:
- First, sensitive data in AWS resources like databases, S3 buckets, and code repositories can be accessed.
- Second, change or delete data, which can seriously disrupt business operations.
- Plus, they can launch malicious attacks against your organization or its customers.
- Finally, they can steal confidential information, compromising intellectual property and customer privacy.
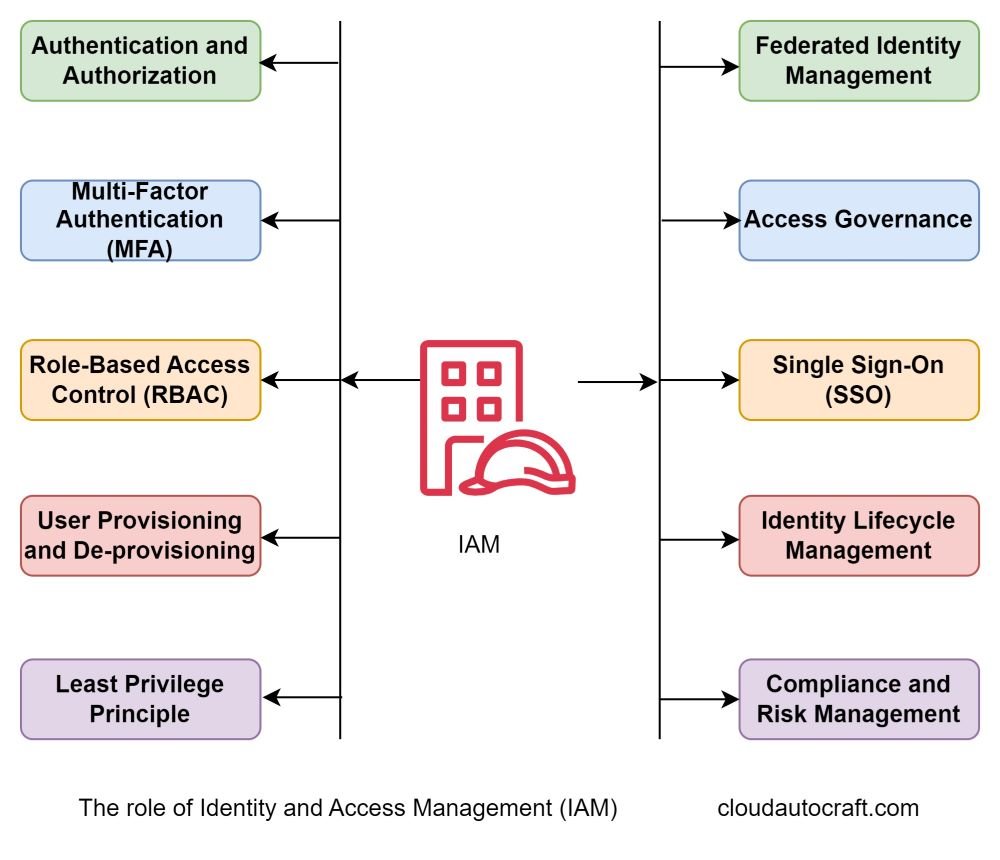
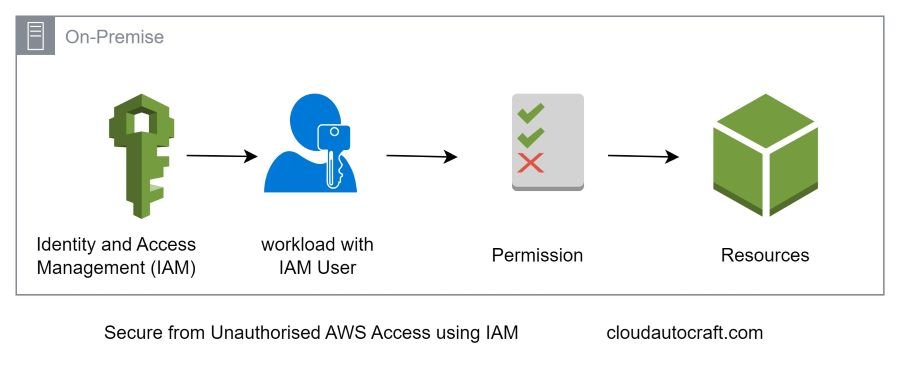
The Role of Identity and Access Management (IAM)
AWS IAM is your first line of defence against unauthorized access. So, It lets you control who can access which resources and under what conditions. However, using IAM policies isn’t enough to manage the risks of unrevoked credentials. You need a complete approach that includes both technical controls and organizational processes.
Key Mitigation Strategies of Unauthorized AWS Access
To reduce the risk of unauthorized access by ex-employees, try these strategies:
| Automated Credential Revocation | Set up automated processes to revoke user credentials when someone leaves the company. You can integrate this with your HR system or use AWS IAM’s features for user lifecycle management. |
| Least Privilege Principle | Give users only the permissions they need for their jobs. So, This limits the damage if an account is compromised. Even if the account isn’t revoked immediately, the impact is lessened. |
| Multi-Factor Authentication (MFA) | Require MFA for accessing AWS accounts. In addition, This adds an extra layer of security, making it harder for unauthorized users to get in. |
| Regular Auditing and Monitoring | Do regular security audits to find vulnerabilities and ensure IAM policies are set up correctly. Continuously monitor AWS access logs to detect suspicious activity and trigger alerts. |
Utilize AWS CloudTrail and CloudWatch
AWS CloudTrail logs API calls and events in your AWS environment. Consequently, CloudWatch monitors resource usage, health, and security events.
These tools give you valuable insights into user activity and help identify potential security threats. You can also set up alerts and notifications for suspicious actions.
Enable AWS Security Hub
Security Hub brings together security findings from different AWS services and third-party tools. Moreover, this gives you a central view of potential security risks, helping you prioritize and fix vulnerabilities and misconfigurations.
With Security Hub, you can also automate security best practice checks. It detects vulnerabilities, misconfigurations, and suspicious activities, providing recommendations for how to fix them.
Implement Network Segmentation
Segmenting your AWS network helps isolate sensitive resources. So this limits access and reduces the impact of security breaches. Use security groups and VPCs to create separate networks for different applications. By controlling traffic and isolating sensitive data, you can improve the overall security of your AWS environment.
Real-World Example: A Case Study
A large online retailer had a data breach because a former employee still had access to their AWS account. The ex-employee used their credentials to steal customer data. Eventually, this incident cost the company millions in fines and legal fees and damaged its reputation.
Leveraging AWS Security Best Practices
AWS offers a range of security features and best practices to protect your cloud infrastructure. However, Key considerations include:
| Security Hub: | AWS Security Hub is a central security management service. Consequently, It gives a unified view of your security posture and automates security tasks. |
| GuardDuty: | AWS GuardDuty is a threat detection service. Consequently, It monitors your AWS environment for malicious activity, like suspicious login attempts and data theft. |
| CloudTrail: | AWS CloudTrail is a logging service. It records all API calls to your AWS account, providing a detailed audit trail for security investigations. |
| Key Management Service (KMS): | AWS KMS securely manages and controls encryption keys to protect sensitive data stored in AWS resources. |
Click this video to learn more about The Best Practices for Unauthorized AWS Access
The Power of Automation
Automation is critical for timely and effective credential revocation. Therefore, AWS offers several tools and services to help with this, including:
| Lambda: | AWS Lambda is a serverless computing service. Moreover, It lets you run code responding to events, like when a user is terminated or resigns. |
| Step Functions: | Second, AWS Step Functions is a workflow service that helps you define and automate complex processes, such as revoking user access and deleting related resources. |
| Systems Manager: | Amazon Web Service Systems Manager is a broad management service. In addition, It provides tools for automating tasks, including credential revocation and resource clean-up. |
Automating these processes reduces the chance of mistakes and ensures that revoked credentials aren’t left active.
Unauthorized AWS Access: Employee Awareness Training
Employee awareness and training are vital in a robust security program. Firstly, it’s essential to teach employees about good password practices. They should also understand the dangers of sharing credentials. Additionally, they need to know how to report suspicious activity. Regular security training helps build a culture of security. As a result, This gives employees the knowledge to protect against threats.
Best Practice with Latest Updated
It’s vital to stay updated on the latest best practices and vulnerabilities to keep ahead in today’s changing security landscape. Hence, Keep learning and adopt new technologies to boost your security. So, Here are some resources to help:
| AWS Security Blog: | Get insights into new threats and best practices for securing your AWS setup. |
| Security Documentation: | Find detailed info on AWS security features, best practices, and compliance requirements. |
| Security Industry Conferences and Events: | In addition, attending Security Conferences and Events lets you connect with experts and learn about emerging threats, keeping you ahead of the game. |
Unauthorized AWS Access: Beyond Credentias
Credential revocation is essential, but it’s just one part of security. Consider these additional measures:
| Cloud Access Security Broker (CASB): | Moreover, This enforces security policies for cloud apps, like those in AWS. It gives visibility and control over data access. |
| Data Loss Prevention (DLP): | Certainly, This stops sensitive data from leaving your AWS setup. |
| Threat Intelligence Sharing: | Sharing threat info with peers and partners is critical. Hence, It helps spot threats early and handle them better. |
The Role of Collaboration for Unauthorized AWS Access
Security involves everyone in your organization working together. Make sure to:
- Work closely with HR to promptly know when employees leave.
- Then, Team up with IT security to set clear rules for managing credentials and who can access what.
Regularly Review and Update Security Measures
In today’s evolving landscape of security threats, it’s vital to continuously review and enhance your security measures to stay proactive against potential risks.
Therefore, Keep yourself updated on emerging vulnerabilities and best security practices. Furthermore, Regularly assess access permissions and policies. Additionally, ensure your security software and configurations are updated periodically to maintain robust protection.
Conclusion
We need a proactive strategy to prevent ex-employees from accessing AWS without permission. Following the steps in this guide can significantly lower the risks linked to departing employees. For more details, check out the AWS IAM Documentation—it has all the info you need!
Click here to Read more about DevOps-Security – 2024 && Cyber Security – 2024
FAQs:
How do we ensure timely revocation of ex-employee access across AWS services?
Answer: To ensure quick access revocation for former employees, we automate the process by linking our HR system with AWS IAM. Consequently, This allows us to promptly deactivate access to all AWS resources when an employee leaves.
How do we balance security and efficiency in revoking access for departing employees?
Answer: Balancing security and efficiency in access revocation means setting clear procedures and using automation effectively. So, By accurately defining roles and permissions and using automated workflows, we swiftly remove access without slowing down operations.
What steps detect and respond to ex-employees attempting Unauthorized AWS Access?
Answer: We monitor and set up alerts to catch ex-employees trying to access without permission. Additionally, Using tools like AWS CloudTrail, we watch closely for any strange activity. If something seems off, we act fast to stop unauthorized access attempts.
How do we effectively communicate and enforce AWS security policies to employees?
Answer: We keep teaching and documenting to ensure everyone follows AWS security rules. Similarly, We run security training often and ensure everyone can easily find our security rules. In addition, we check regularly and remind everyone to stick to the rules.
Originally posted 2024-06-21 12:53:32.


10 thoughts on “How to Secure Unauthorized AWS Access by Ex-Employees”