Content:
Introduction
Kubernetes has really transformed how we deploy and manage applications. However, with this power, security becomes a big responsibility. As your Kubernetes setup grows more complex, having the right Kubernetes Security Tools is crucial to protect your infrastructure and data. Therefore, in this post, we’ll guide you on choosing the best Kubernetes security tools for your needs.
Understanding Kubernetes Security Tools Challenges
Before we get into the tools, let’s take a look at some common security challenges you might encounter in a Kubernetes environment:
- Container Vulnerabilities: Containers can be a weak link in security if not handled properly. So, they can be vulnerable to threats like misconfigured images, outdated software, or malicious code. Moreover, These issues can make your containers susceptible to attacks. Hence, It’s important to manage them carefully to maintain security.
- Network Security: It’s vital to secure communication between your Kubernetes components, pods, and external services. Without proper safeguards, you risk unauthorized access or data breaches. These issues can have serious consequences.
- Privileged Access Management: Managing who can access your Kubernetes resources—like clusters, namespaces, and APIs—is vital. Moreover, this helps you to reduce the risk of insider threats or unauthorized access that could compromise your system.
- Compliance and Regulatory Requirements: Depending on your industry and location, you may have to adhere to specific security standards and regulations. Therefore, this can add complexity to your Kubernetes security strategy, making it essential to choose tools that help you stay compliant.
Top Considerations for Kubernetes Security Tools Selection
When choosing Kubernetes security tools, it’s important to keep several factors in mind:
- Security Coverage: To start, You have to make sure that tools cover all your bases—container image scanning, network traffic monitoring, access control, and compliance. It would help if you addressed the full range of security needs.
- Integration and Scalability: Furthermore, look for tools that easily fit into your existing Kubernetes setup. They should also scale as your environment grows, ensuring continuous protection as you expand.
- Ease of Use: Additionally, go for tools that are simple to use. An intuitive interface and easy setup can save time and make it easier for your team to adopt.
- Visibility and Reporting: Moreover, it’s crucial to have a clear view of what’s happening in your Kubernetes environment. Therefore, Tools with real-time monitoring, alerts, and detailed reports can help you stay on top of potential issues.
- Vendor Support and Community: Lastly, check the vendor’s reputation and see if they have a strong user community. However, Good support and a vibrant community can make a big difference in the long-term success and usability of the tool.
Top Kubernetes Security Tools to Consider
Let’s explore some popular Kubernetes security tools and see how they can help keep your environment secure:
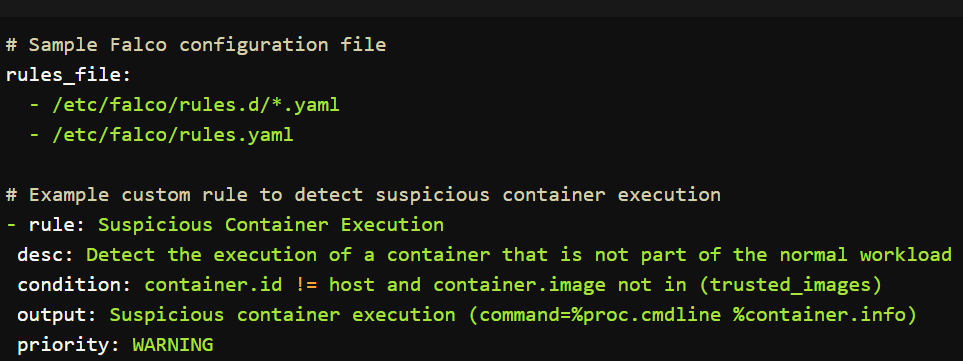
Falco:
- What it does: Falco is an open-source tool that provides real-time security monitoring for your Kubernetes clusters. It alerts you to unusual activities that could signal a security issue.
- How it works: It monitors your system calls, file access, network activity, and other runtime events to catch potential threats.
- Customization: You can tweak its rules to match your specific security needs, making it highly adaptable.
Aqua Security
- Overview: Aqua Security provides a complete platform for securing your Kubernetes setup. It covers everything from scanning container images to runtime protection and access control.
- Key Features: The platform offers features like vulnerability scanning, policy-based access controls, and anomaly detection, which give users a strong defence against potential threats.
- Integration: Aqua Security works seamlessly with popular Kubernetes tools and gives you detailed visibility into your security status, making it easier to manage and monitor your environment.
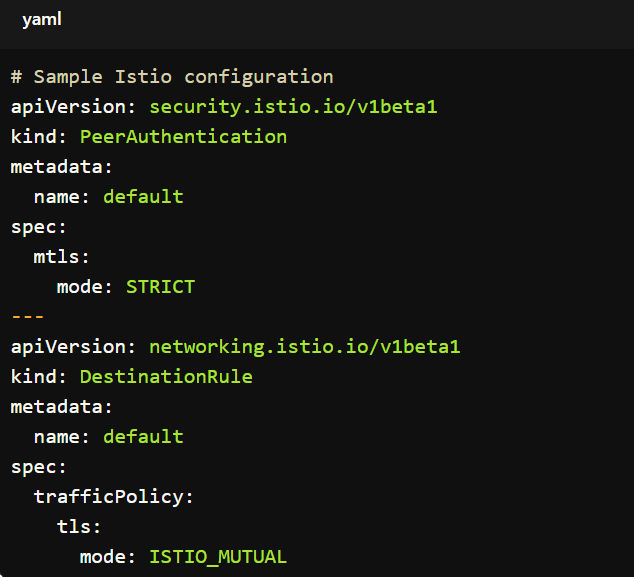
Istio
- Purpose: Istio is an open-source service mesh that enhances security and observability for your Kubernetes applications.
- Capabilities: It offers features like mutual TLS authentication, traffic management, and policy enforcement. These help secure and manage communication between microservices.
- Best Practices: Istio supports security best practices, including zero-trust networking and end-to-end encryption.
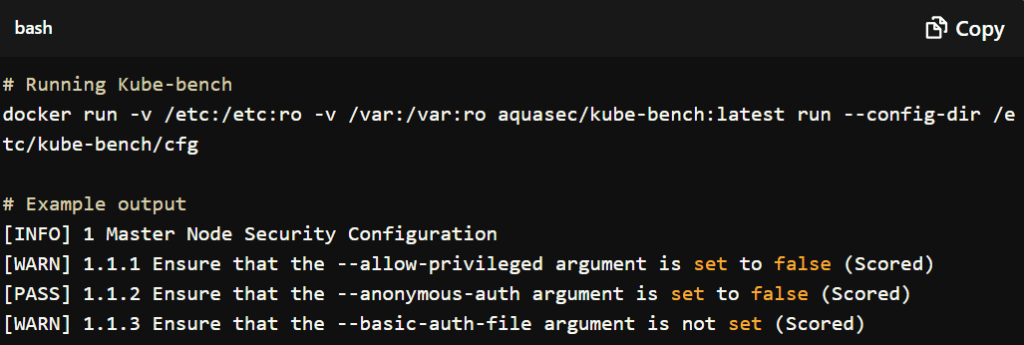
Kube-bench
- Functionality: Kube-bench checks your Kubernetes clusters against the Center for Internet Security (CIS) Kubernetes Benchmark standards.
- Benefits: It scans for misconfigurations and vulnerabilities, helping you fix potential security issues.
- Integration: You can integrate Kube-bench into your CI/CD pipeline to continuously monitor and maintain a secure configuration.
Trivy:
- Use Case: Trivy is an open-source scanner for container images, file systems, and Git repositories.
- Versatility: It works with various container runtimes and cloud providers, making it a versatile tool for securing your Kubernetes setup.
- Automation: Trivy can be integrated into your CI/CD pipeline to scan for vulnerabilities in container images before deployment automatically.
Fluentd:
- Functionality: Fluentd is like your personal assistant for handling logs in your Kubernetes environment. It gathers, processes, and forwards logs from various parts of your system. Plus, it’s smart enough to handle different data formats and can even transform logs to make them easier to analyze.
- Benefit: With Fluentd, all your logs are centralized and standardized. Moreover, This makes troubleshooting a breeze and gives you a clear view of what’s happening in your system. It also helps you stay compliant by keeping a neat and auditable trail of all your logs.
- Integration: Fluentd works great with data stores and analytics tools like Elasticsearch, Splunk, and cloud-based log management services. Therefore, you can store, query, and visualize your logs efficiently. Furthermore, if you’re using other monitoring tools like Prometheus and Grafana, Fluentd fits right in, giving you a complete observability stack.
By using Fluentd, you make log management simpler and more effective, turning a complex task into a smooth and manageable process.
Prometheus and Grafana:
- Monitoring: Prometheus is a fantastic open-source tool for monitoring and alerting. It’s ideal for tracking the health and performance of your Kubernetes clusters.
- Visualization: Grafana is a powerful data visualization and dashboard tool. When used alongside Prometheus, it provides detailed insights into your Kubernetes environment, helping you visualize and understand your data more clearly.
- Security Monitoring: Together, they help you spot security-related events, such as unauthorized access, resource exhaustion, and network anomalies, making your monitoring efforts more comprehensive and effective.
Click here to get more insight about: How to Implement Cloud Native DevOps with Kubernetes
Implementing a Kubernetes Security Tools Strategy
After selecting the right Kubernetes security tools for your Kubernetes environment, it’s crucial to set up a comprehensive security strategy. Therefore, here are the key areas to focus on:
Container Image Security:
- First and foremost, regularly scan your container images for vulnerabilities.
- Additionally, enforce policies that only allow trusted images to be deployed, reducing the risk of introducing vulnerabilities into your environment.
Network Security:
- Furthermore, You should set up network policies, firewalls, and encryption to secure communications between Kubernetes components and external services.
- Implement network segmentation to isolate sensitive workloads and minimize the attack surface.
Access Control and Authorization:
- Moreover, role-based access control (RBAC) and other access management tools should be used to limit and monitor who can access Kubernetes resources.
- Implement least privilege principles to ensure users and services only have the necessary access.
Logging and Monitoring:
- In addition, use tools like Prometheus and Grafana to monitor your Kubernetes environment continuously.
- These tools help detect anomalies and alert you to security-related events, enabling proactive incident management.
Incident Response and Remediation:
- Furthermore, It’s essential to have a clear incident response plan ready to go.
- You must ensure that your security tools are set up to help you quickly investigate and resolve any security incidents. However, this will help minimize the impact on your operations and keep things running smoothly.
Compliance and Regulatory Requirements:
- Lastly, you must ensure that your Kubernetes security measures meet industry standards and regulations, such as HIPAA, PCI-DSS, or GDPR.
- Finally, Reviewing and updating your security practices regularly is essential to stay compliant as regulations change. Keeping up with these updates helps protect your organization and ensures you follow the latest guidelines.
Conclusion of Kubernetes Security Tools
Securing your Kubernetes environment is crucial. However, with the right tools and a solid strategy, you can significantly reduce risks and protect your applications and data. By keeping the key factors we’ve discussed in mind and exploring top Kubernetes security tools, you’ll be on the right track to building a strong and resilient security setup.
Additionally, remember that the Kubernetes security landscape is always changing. Therefore, staying up-to-date with the latest trends, best practices, and tool updates is essential. Regularly reviewing and refining your security strategy will help you stay protected against new and emerging threats. In summary, continuous improvement and vigilance are key to maintaining a strong security posture.
Click here to get more insight about: How to Enhance More Kubernetes for App Deployment
FAQs:
Why is Kubernetes Security Tools so Important?
Answer: Kubernetes security is vital because it protects your applications, data, and infrastructure from cyber threats. Moreover, if there are vulnerabilities in your Kubernetes setup, it could lead to data breaches, unauthorized access, or even system compromises. That’s why it’s essential to have strong security measures in place to keep your organization safe.
How can I Effectively Detect and Prevent Kubernetes Threats?
Answer: Effective Kubernetes threat detection and prevention require a multi-layered approach. It would help if you used proper configuration and security tools like Kube-bench, Falco, and Istio. Additionally, network policies should be implemented, and strong access controls should be set up. Moreover, these steps help minimize the attack surface and allow you to quickly spot and respond to any suspicious activity, ensuring a robust security posture.
What are the Top Kubernetes Security Tools Vulnerabilities You Should be Aware of?
Answer: Common Kubernetes security vulnerabilities include misconfigured API servers, insecure container images, privilege escalation, exposed sensitive data, and outdated Kubernetes versions. Therefore, it’s crucial to stay informed about these issues and address them promptly to improve your Kubernetes security posture. By proactively managing these vulnerabilities, you can better protect your infrastructure and data from potential threats.
How to Implement Kubernetes Security Tools for Monitoring and Incident Response?
Answer: To set up effective Kubernetes security monitoring and incident response, consider using tools like Falco for anomaly detection, Prometheus for metrics collection, Grafana for visualization, Fluentd for centralized logging, and Kube-bench for configuration auditing. Consequently, this integrated approach not only gives you visibility but also helps quickly detect and respond to security incidents in your Kubernetes environment, enhancing your overall security posture.
Originally posted 2024-07-28 20:51:26.


5 thoughts on “Best Kubernetes Security Tools: How to Choose!”