Content
- Introduction
- Why Container Security Tools is Critical
- Key Features to Look for in Container Security Tools
- Top 10 Container Security Tools
- Detailed Review of Aqua Security
- Why Sysdig Secure is Perfect for Kubernetes
- How Prisma Cloud Provides Comprehensive Container Security Tools
- Emerging Trends in Best Container Security Tools
- Best Practices for Implementing Best Container Security Tools
- How to Choose the best Container Security Tools for Your Organization
- Common Mistakes to Avoid with Best Container Security Tools
- The Future of Best Container Security Tools
- Conclusion: Container Security Tools
- FAQs:
Introduction
Container technology has transformed application development, making it faster and more efficient. However, securing containerized environments has become increasingly important as threats evolve rapidly. Container security involves safeguarding containers throughout their lifecycle, from build to runtime. Whether using Docker or Kubernetes, the demand for effective best container security tools is greater than ever. In this blog, we will explore the leading tools that ensure the security of these modern environments.
Why Container Security Tools is Critical
Container security is becoming increasingly crucial. While containers provide scalability, portability, and faster deployment, these benefits also make them attractive targets for cybercriminals.
Containers decompose monolithic applications into smaller microservices, simplifying development but complicating security. As cyber threats become more sophisticated, securing these fragmented components is essential.
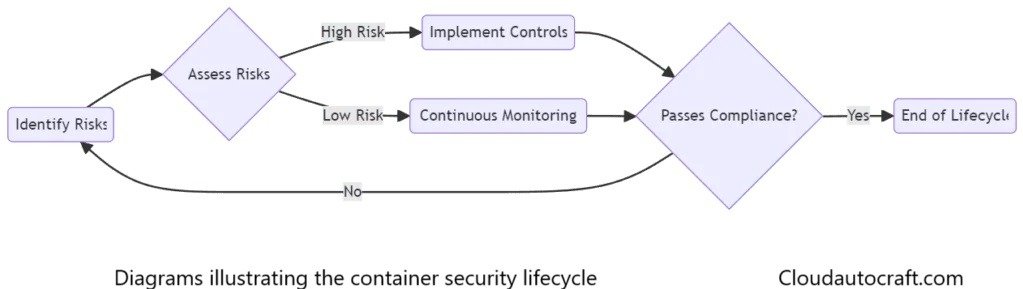
Businesses must implement comprehensive security solutions that address all aspects of their containerized environments, from image scanning to runtime protection. Remember, just one vulnerability can compromise your entire system.
Key Features to Look for in Container Security Tools
Before we explore the top tools, it’s essential to understand what makes a container security tool effective. Not all tools are created equal, and each one comes with its unique set of features. However, there are some must-haves that you should look for when evaluating these tools.
- Vulnerability Management – Can the tool scan your containers for vulnerabilities before deployment? This is critical because you want to catch weaknesses before they become entry points for attacks.
- Runtime Protection – Does the tool offer real-time monitoring? It’s not enough to scan images once. Containers need continuous oversight to detect any anomalies or unauthorized changes while they’re running.
- Compliance – Does the tool ensure that your containerized environments meet industry regulations? Compliance isn’t just about security; it’s also about avoiding fines and penalties.
- Network Segmentation – Can the tool isolate containers to prevent lateral movement in case of a breach? Network segmentation can limit the damage even if one container is compromised.
- Access Control – Does it provide fine-grained access control to ensure only authorized users can modify or deploy containers?
With these features in mind, let’s take a closer look at the tools that excel in protecting containers in 2024.
Overview of Container Security Tools Technologies
Docker Security Essentials
Docker continues to be one of the most popular container platforms, widely used for its ease of use and portability. But here’s the thing—Docker alone isn’t inherently secure. You need to adopt certain practices to ensure your Docker containers are protected.
One of the first steps in securing Docker environments is to scan images for vulnerabilities. Additionally, enforcing proper access controls and isolating containers from one another can go a long way in preventing unauthorized access or privilege escalation.
Kubernetes Security Challenges
Kubernetes, on the other hand, takes containerization to the next level with its orchestration capabilities. However, this added complexity also brings new security challenges. With Kubernetes, you need to secure not just individual containers but also the communication between them.
Some common security concerns in Kubernetes include securing pod-to-pod communications, implementing role-based access control (RBAC), and ensuring that Kubernetes configurations aren’t exposing sensitive data or creating vulnerabilities.
Other Emerging Container Platforms
While Docker and Kubernetes dominate the container space, other platforms like OpenShift and GKE (Google Kubernetes Engine) are also gaining traction. Each platform has its own nuances when it comes to security, but the core principles remain the same: protect the build, deployment, and runtime stages of your containers.
Click here to get more about Top 10 Tools for Docker Security Automation You Need to Know || Best Kubernetes Security Tools: How to Choose!
Top 10 Container Security Tools
Now that we have a solid understanding of container technology and its security challenges, let’s explore the top tools that are making waves in 2024.
Aqua Security
If you’re looking for an all-in-one solution for container security, Aqua Security is a top contender. It provides end-to-end security, covering everything from vulnerability scanning to runtime protection. Aqua integrates seamlessly with both Docker and Kubernetes environments, making it a versatile option for organizations of all sizes.
Sysdig Secure
Sysdig Secure shines when it comes to real-time monitoring and visibility, particularly in Kubernetes environments. One of its standout features is its deep integration with Kubernetes, which allows you to detect and respond to security threats as they happen. If Kubernetes is your container platform of choice, Sysdig Secure is definitely worth considering.
Prisma Cloud
Prisma Cloud, formerly known as Twistlock, is another comprehensive solution that covers a wide range of container security needs. Here, Prisma Cloud is designed to protect not just containers but also serverless functions and hosts. This makes it an excellent option for organizations that are using a mix of different cloud-native technologies.
StackRox (Red Hat Advanced Cluster Security)
StackRox, which has now been integrated into Red Hat’s Advanced Cluster Security for Kubernetes, focuses on Kubernetes-native security. It provides deep visibility into Kubernetes environments, allowing you to enforce security policies and detect misconfigurations. StackRox’s integration with Kubernetes makes it one of the best tools for organizations heavily invested in this platform.
Twistlock (Prisma Cloud)
Twistlock, now part of Prisma Cloud, offers a robust set of security features that include vulnerability scanning, compliance checks, and runtime protection. Its ability to secure the full lifecycle of containers makes it a favorite among DevOps teams that prioritize both security and efficiency.
Anchore
Anchore is a popular open-source tool that specializes in container image scanning. It’s perfect for organizations that are looking for a low-cost option that can be easily integrated into their CI/CD pipelines. Anchore helps ensure that your container images are free from vulnerabilities before they ever make it to production.
NeuVector
NeuVector stands out for its focus on network security within container environments. It provides real-time protection against network-based threats by inspecting and analyzing container traffic. If you’re looking for a tool that specializes in securing container networks, NeuVector is a great choice.
Qualys Container Security
Qualys has been a trusted name in the security world for years, and its container security tool doesn’t disappoint. It offers image scanning, runtime protection, and compliance monitoring—all critical components of a strong container security strategy.
Falco
Falco, an open-source project by the Cloud Native Computing Foundation (CNCF), provides real-time threat detection for containerized environments. It’s lightweight, easy to integrate, and great for organizations that want a free yet powerful security solution.
Clair
Clair is another excellent open-source option that specializes in static vulnerability analysis for container images. It’s ideal for small to mid-sized projects looking for an efficient way to scan images before they’re deployed.
Detailed Review of Aqua Security
Aqua Security continues to lead the market with its comprehensive approach to container security. What sets Aqua apart is its ability to secure containers at every stage—from image scanning to enforcing runtime policies. Whether you’re using Docker, Kubernetes, or a hybrid environment, Aqua has you covered. Its powerful compliance features ensure that your organization meets industry standards, making it particularly attractive for enterprises.
Why Sysdig Secure is Perfect for Kubernetes
If your infrastructure relies heavily on Kubernetes, Sysdig Secure is a must-have. Its real-time monitoring capabilities provide full visibility into Kubernetes clusters, helping you detect and mitigate threats as they arise. One of its standout features is its integration with Falco, allowing you to tap into the power of open-source threat detection while benefiting from Sysdig’s enterprise-grade support.
How Prisma Cloud Provides Comprehensive Container Security Tools
Prisma Cloud takes container security a step further by offering protection not just for containers but for the entire cloud-native stack. This includes serverless functions, VMs, and Kubernetes clusters. Its unified dashboard provides a comprehensive view of your cloud infrastructure, making it easier to manage and secure.
Emerging Trends in Best Container Security Tools
As we move further into 2024, several trends are shaping the future of container security. One of the most significant is the shift toward more integrated security solutions. Rather than relying on multiple tools for different aspects of security, organizations are looking for platforms that offer end-to-end protection.
Additionally, there is a growing emphasis on automation. With the rapid pace of development in containerized environments, manually securing each container is no longer feasible. Tools that offer automated vulnerability scanning and threat detection are becoming increasingly popular.
Another emerging trend is the rise of AI-powered security tools. These tools use machine learning algorithms to identify patterns in container behaviour, allowing them to detect anomalies and potential threats in real time.
Best Practices for Implementing Best Container Security Tools
Implementing container security might seem overwhelming at first, but it doesn’t have to be. Here are a few effective strategies to get you started:
- Scan Images Early and Often – Don’t wait until containers are deployed to start scanning for vulnerabilities. Implement scanning at every stage of development to catch issues before they become serious threats.
- Enforce Least Privilege – Make sure that containers only have the access they need to function. Limiting privileges can significantly reduce the risk of unauthorized access or privilege escalation.
- Use Network Policies – Segment your container networks to prevent lateral movement in case one container is compromised.
- Monitor Runtime Behavior – Continuous monitoring is key to detecting anomalies or unauthorized changes. Use tools like Falco to get real-time visibility into your container environments.
- Implement Role-Based Access Control (RBAC) – Ensure that only authorized users can modify or deploy containers. RBAC is an essential component of container security.
How to Choose the best Container Security Tools for Your Organization
With so many options available, how do you choose the right container security tool for your organization? Start by assessing your current infrastructure and security needs. Are you running mostly Docker containers, or is Kubernetes your primary platform? Do you need end-to-end security, or are you looking for a specific solution like image scanning?
Next, consider your budget. Open-source tools like Falco and Clair can provide excellent security at no cost, but paid solutions like Aqua Security and Prisma Cloud offer more advanced features and support.
Finally, think about scalability. As your organization grows, your container security needs will evolve. Choose a tool that can scale with you and adapt to new challenges as they arise.
Common Mistakes to Avoid with Best Container Security Tools
When it comes to container security, even the most well-intentioned teams can make mistakes. Here are a few frequent mistakes to steer clear of:
- Not Scanning Images Regularly – Some teams only scan container images once and assume they’re secure. In reality, vulnerabilities can be introduced at any stage of development, so it’s important to scan images continuously.
- Ignoring Runtime Security – Image scanning is important, but it’s not enough. Containers need to be monitored in real-time to detect anomalies or unauthorized changes.
- Failing to Segment Networks – Containers should be isolated from one another to prevent lateral movement in case of a breach.
- Overlooking Compliance Requirements – Compliance isn’t just about security; it’s also about avoiding fines and penalties. Make sure your container environments meet industry regulations.
- Not Implementing RBAC – Giving too many people access to container environments can increase the risk of unauthorized changes or breaches. Implement Role-Based Access Control (RBAC) to restrict access, ensuring only authorized users can interact with specific resources.
The Future of Best Container Security Tools
As we look to the future, container security will continue to evolve. In 2025, we can expect to see more integrated security solutions that offer end-to-end protection for the entire cloud-native stack. Automation and AI will also play a larger role in detecting and mitigating threats in real time.
Additionally, we’ll likely see an increased focus on securing not just containers but also the platforms that run them, such as Kubernetes and OpenShift. As container adoption continues to grow, so too will the need for more sophisticated security solutions.
Conclusion: Container Security Tools
In 2024, container security is no longer optional—it’s a necessity. With cyber threats evolving rapidly, organizations must invest in comprehensive security solutions that protect containers at every stage of their lifecycle. From image scanning to runtime protection, the tools we’ve discussed in this article offer a wide range of features to meet the unique needs of any organization.
By following best practices and choosing the right tools, you can ensure that your container environments remain secure and compliant. Whether you’re running Docker, Kubernetes, or a hybrid environment, there’s a container security tool out there that’s perfect for your needs.
Click here to get more about Cloud-Computing || Cyber-Security
FAQs:
What are the key security challenges in managing containers?
Answer: The main challenges include, first and foremost, securing container images from vulnerabilities. Additionally, managing secure network communication between containers is crucial. Furthermore, controlling access to orchestration platforms like Kubernetes is essential, as is ensuring runtime security by detecting and blocking abnormal behaviour within containers.
How do best container security tools integrate with DevOps pipelines?
Answer: Best Container security tools integrate seamlessly into CI/CD pipelines by scanning images for vulnerabilities during the build process. Moreover, they enforce security policies automatically, working with platforms like Jenkins to prevent insecure code from reaching production. This integration enables early risk detection and ensures compliance throughout the development lifecycle.
Which container security tool is best for Kubernetes environments?
Answer: For Kubernetes environments, Prisma Cloud and Aqua Security are top picks. Both tools provide end-to-end protection, including vulnerability scanning and compliance enforcement. In addition, they offer runtime monitoring with deep integration into Kubernetes, ensuring that containerized applications remain secure.
How do container security tools handle runtime protection?
Answer: Container security tools, such as Falco and Aqua Security, monitor container activity in real time, thereby detecting anomalies or policy violations. They establish baselines for normal behavior, alerting users on suspicious activity. Additionally, they can isolate compromised containers to prevent further threats, enhancing overall security.
Originally posted 2024-10-02 00:21:05.

