In today’s digital world, evolving cyber threats make security a top priority. Automating security processes is crucial for staying ahead, but finding the right approach can be challenging. This article explores strategies and best practices for Streamline Security Automation to enhance your organization’s protection and response capabilities.
Content:
- Unlock the Power of Streamline Security Automation
- Streamline Security Automation Incident Response:
- Streamline Security Automation Orchestration and Response
- Streamline Security Automation Monitoring Approach
- The Future of Streamline Security Automation:
- Success Stories of Streamline Security Automation
- Conclusion
- FAQs:
Unlock the Power of Streamline Security Automation
Automating security tasks can significantly enhance your operations, reduce errors, and empower your security team to tackle more strategic initiatives. While the process of setting up security automation may not be straightforward, the benefits it brings are worth the effort.
Here are some challenges that many organizations encounter when implementing security automation:
- Lack of Integration: Often, different security tools work in isolation, making it hard to create a seamless automation workflow. Therefore, this can lead to inefficiencies, mixed-up data, and more risk.
- Complexity of Implementation: Getting security automation up and running can be tricky, especially if your organization needs more resources or expertise.
- Difficulty in Scaling: Keeping your security automation effective and scalable can take time and effort as your organization grows and threats evolve. It requires regular tweaks and updates.
- Concerns about Flexibility: Some organizations worry that embracing security automation might make adapting to changing needs or unique situations harder.
To streamline security automation, consider using a centralized security platform. Therefore, this approach helps in several ways:
Adopt a Centralized Security Platform
One of the most effective ways to streamline security automation is by adopting a centralized security platform that integrates various security tools and technologies. This approach allows you to:
- Unify Data Sources: A centralized security platform brings together data from various security tools. This unified view makes it easier to understand the security landscape and make informed decisions.
- Streamline Workflows: With automation features, these platforms create smooth, end-to-end workflows. So, they connect different security tools and processes, making security operations more straightforward.
- Improve Visibility: Using a centralized platform gives you a clear, comprehensive view of your security posture. Moreover, this makes it easier to spot and address vulnerabilities.
Adopting a DevSecOps Mindset
Embracing a DevSecOps approach can significantly enhance your security automation efforts. Here are some ways you can benefit from this mindset:
- Shift Security Left: Incorporate security checks and controls early in the development process. This proactive strategy, known as “shifting left,” helps identify and address vulnerabilities sooner, saving time and reducing costs associated with later-stage fixes.
- Automate Security Testing : Integrate automated security testing into your CI/CD (Continuous Integration/Continuous Deployment) pipeline. By doing so, security assessments and validations become a continuous part of the development cycle, ensuring that vulnerabilities are detected and addressed promptly as new code is developed and deployed.
- Foster Collaboration: Encourage collaboration between your security, development, and operations teams. This cross-functional teamwork ensures that security considerations are integrated into every stage of the software
Enhancing Security Automation with AI and ML
Utilizing AI and ML technologies can significantly enhance your security automation capabilities. Therefore, here are some key benefits:
- Enhance Threat Detection: AI-powered tools can filter through vast data to spot patterns and anomalies that might signal a security threat. This advanced analysis means faster and more accurate threat detection, helping to protect your systems from potential breaches
- Optimize Incident Response: Machine learning (ML) algorithms can automate different stages of handling security incidents, from triage to investigation and remediation. By streamlining these steps, AI and ML make incident response quicker and more reliable, saving time and effort in managing security issues and allowing you to focus on more strategic tasks.
- Improve Vulnerability Management: AI and ML can assist in prioritizing vulnerabilities based on their severity and the likelihood of exploitation. This prioritization helps focus your patching and remediation efforts on the most critical issues, optimizing your overall security posture and resource allocation, and making you feel more strategic and resourceful in your work.
Prioritize Flexibility and Scalability
As your organization grows and threats change, your security automation must adapt. Therefore, here’s how you can make sure it scales with your needs:
- Modular Design: Build a flexible system. Moreover, this lets you easily add new security tools and technologies when needed.
- Scalable Processes: You can create workflows that can handle more data and security events. And, Ensure they don’t slow down or lose reliability as things grow.
- Continuous Optimization: Finally, you should regularly check and update your security automation. Keep it aligned with your organization’s changing needs and the latest industry practices.
Foster a Culture of Security Awareness
Security automation goes beyond technology; it involves cultivating a robust security culture within your organization. Therefore, here’s how to promote this mindset:
- Employee Training: Ensure your company provides regular security training sessions. So, help your team understand best practices, recognize common threats, and know their role in securing things.
- Collaborative Mindset: You should encourage a team-focused approach to security. Therefore, let everyone know that maintaining security is a shared responsibility, not just the security team’s job. Eventually, this kind of shared ownership makes the whole organization more proactive and alert.
- Feedback and Continuous Improvement: Set up ways for employees to share their thoughts on security practices and automation strategies. However, use their feedback to improve your organization’s security measures and keep up with real-world challenges and experiences.
Streamline Security Automation Incident Response:
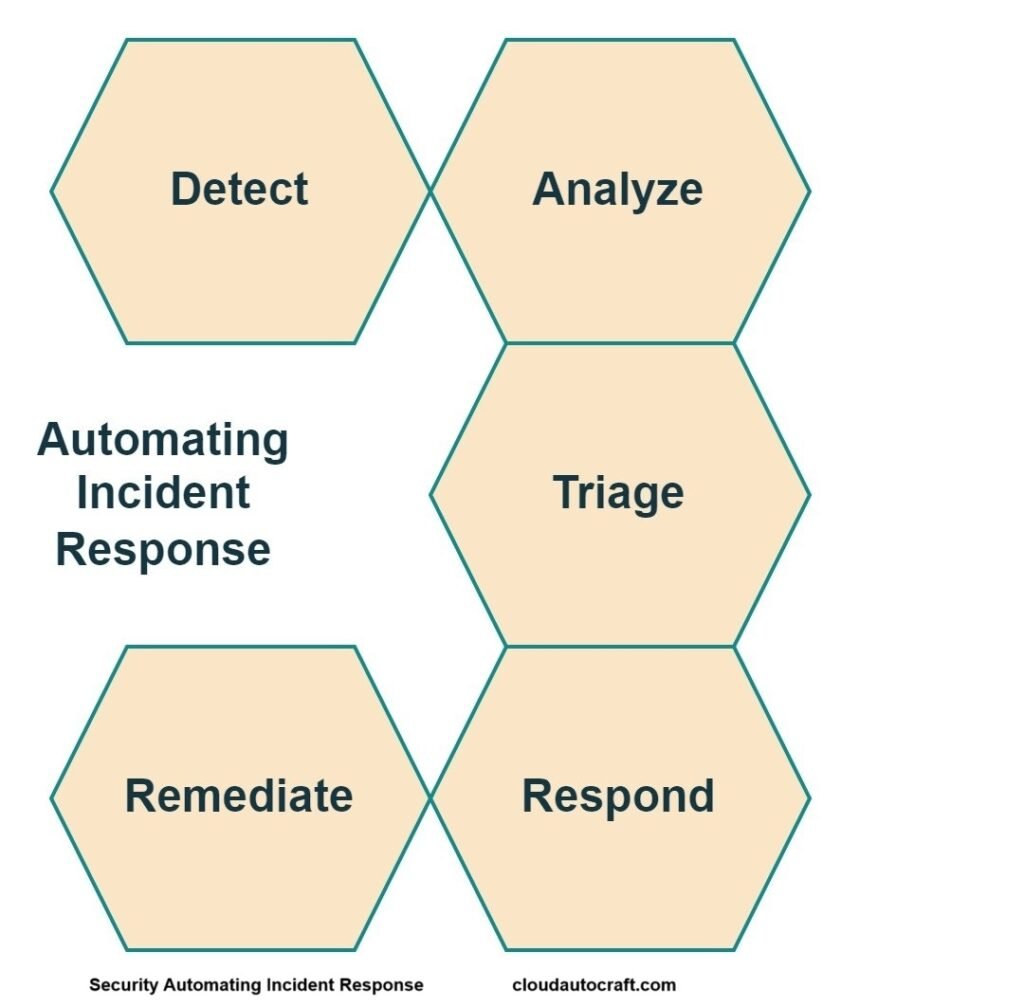
List of Incident Responses mentioned below which your organization should follow:
- Detect: First and foremost, automated security tools constantly monitor the network, applications, and user activities. Consequently, they quickly spot potential security incidents.
- Analyze: Following detection, security automation solutions analyze these events. By combining data from different sources, they understand the scope and severity of the incident.
- Triage: Subsequently, automated triage processes prioritize incidents based on set risk criteria. This approach ensures that the most critical issues are addressed first.
- Respond: Next, automated responses can be triggered to counter threats. Actions such as quarantining infected devices, blocking suspicious IP addresses, or initiating incident response workflows can be taken promptly.
- Remediate: Finally, automated remediation steps are executed. Moreover, This includes applying security patches, restoring from backups, or removing malware to resolve the underlying issues.
Streamline Security Automation Orchestration and Response
Security Orchestration and Automated Response (SOAR):
Security Orchestration and Automated Response (SOAR) SOAR platforms are a game-changer for integrating and coordinating different security tools and technologies. They make it easier to manage your security operations and automate those tricky incident response workflows.
With SOAR, your security team can respond to threats more quickly, cut down on the time it takes to spot and fix issues, and overall, improve your security. It’s like having a supercharged system that helps you stay on top of potential problems.
Key Benefits of SOAR:
- Centralized Security Visibility
- Automated Threat Response
- Improved Incident Response Times
- Enhanced Collaboration and Coordination
- Comprehensive Reporting and Analytics
Implementing a SOAR Solution:
When embarking on implementing a SOAR solution, organizations should carefully consider their specific security needs, existing tools, and the level of integration required. It’s imperative to ensure that the SOAR platform seamlessly connects with the organization’s security ecosystem and provides a centralized view of security operations.
Streamline Security Automation Monitoring Approach
- Continuous Monitoring: Security automation tools are like vigilant watchdogs for your systems. So, they constantly scan for any unusual activity or potential threats, ensuring problems are caught before they can do any harm.
- Real-Time Analysis: These tools immediately jump into action when they spot a potential threat. Furthermore, they analyze the data to determine where the danger came from, what it’s trying to do, and how serious it is. Finally, this quick analysis helps us prioritize what must be done to prevent further damage.
- Efficient Incident Response: Automation finds threats and helps us respond quickly and effectively. In particular, It can automatically isolate affected systems, block harmful traffic, or even shut down attacks before they get out of hand.
- Analytics for Improvement: Besides handling immediate threats, security automation gives us valuable insights. It tracks trends, spots vulnerabilities, and measures how well our security measures work. Moreover, this helps us continuously improve our defences over time.
The Future of Streamline Security Automation:
Increased Integration: As security evolves, we’ll likely see our automation tools connecting more with different parts of our systems. Therefore, this means better integration with IT services, cloud platforms, and access management. It’ll help everything work together more smoothly.
Advancements in AI and ML: AI and machine learning keep getting better. Therefore, this means our security tools will also become more competent. They’ll learn from new data and get better at spotting emerging threats, helping us stay ahead of potential issues.
Autonomous Security: In the future, we might see security systems that handle a lot of tasks on their own. Imagine systems that can detect problems, understand what’s happening, and even take action without us always needing to step in. It’ll make security operations faster and more efficient.
Success Stories of Streamline Security Automation
| Industry | Challenge | Solution | Results |
| Healthcare | In the healthcare sector, staying compliant with industry regulations and protecting sensitive patient information from cyber threats is crucial. | We’ve implemented automated vulnerability management and patch deployment solutions to tackle this. These tools continuously monitor and fix vulnerabilities across the organization. | As a result of our efforts, we’ve significantly enhanced our compliance reporting. This means you can have full confidence in the transparency and accuracy of our operations. We’ve also managed to reduce the risk of data breaches and free up IT resources for more strategic initiatives. |
| Financial Services | In the financial services industry, it’s all about quickly spotting and dealing with security incidents to protect customer data and avoid financial losses. | We’ve rolled out a SOAR platform to help with this. It automates incident response, integrates various security tools, and offers real-time threat detection and analysis. | As a result, We’ve cut incident response time by 70%, boosted our security team’s productivity, and strengthened our security stance. |
| Manufacturing | In the manufacturing sector, it’s essential to streamline security operations and maximise limited resources to protect operational technology (OT) and industrial control systems. | By enhancing visibility into the OT network, we’ve improved how quickly we can respond to incidents and allowed our security team to tackle emerging threats more proactively. | This increased visibility means faster incident response times and a better ability to address new threats before they escalate. |
Conclusion
In conclusion, finding the best way to streamline security automation is critical for any organization wanting to boost its cybersecurity. To build a robust security framework, you must assess what you need, choose the right tools and technologies, and encourage teamwork between your security and IT teams. Using automation can significantly improve how you detect and respond to threats. It also makes your operations more efficient and cuts down on manual errors. As cybersecurity threats keep changing, focusing on automation will be more critical than ever. It helps protect your digital assets and manage risks effectively.
Click here to Read more about How to AI-Driven Automation Works && Quick Delivery with Shift-Left Testing
FAQs:
What are the key methods for initiating security automation?
Answer: There are several effective methods to consider when diving into security automation. First, figure out where automation can make the most significant difference. Identify the areas where your security could be more robust, such as specific vulnerabilities or potential threats. This way, you can customize your automation strategy to tackle these issues directly.
How can businesses effectively implement automated security measures?
Answer: Implementing automated security measures takes careful planning and execution. Start by evaluating your current security setup. Look for areas where automation could make things smoother and more efficient. Then, choose the right tools and technologies that fit your organization’s needs and goals.
What are the benefits of integrating automation into security protocols?
Answer: Integrating automation into your security protocols offers many benefits. It boosts your ability to detect and respond to threats while freeing up time and resources for your security team to focus on more strategic tasks. In addition, automation ensures consistency and accuracy in security processes, which helps reduce the risk of human error.
Originally posted 2024-05-02 12:14:02.


4 thoughts on “What’s the Best Way to Streamline Security Automation”