Content
- Introduction
- Understanding the Landscape of Secure Data Breaches
- Implementing Robust Data Security Measures
- Preparing for the Inevitable: Secure Data Breaches Planning
- Restoring Trust and Rebuilding Reputation for Secure Data Breaches
- The Role of Leadership in Secure Data Breaches
- Navigating the Legal and Regulatory for Secure Data Breaches
- Emerging Trends and Future Considerations of Secure Data Breaches
- Secure Data Breaches: A Comprehensive Approach
- Incident Response and Reputation Management for Secure Data Breaches
- Conclusion: A Call to Action
- FAQs:
- What are the most common vulnerabilities that cybercriminals exploit to initiate Secure Data Breaches?
- What legal implications do data breaches have, and how can businesses navigate them?
- How can businesses take to detect and respond to insider threats that may lead to data breaches?
- What immediate steps should a business take after a data breach to protect sensitive information?
Introduction
A global enterprise discovers that cyber attackers have breached its customer database, which holds millions of personal records. This discovery raises significant concerns about data privacy and identity theft risk. So, how do you handle Secure Data Breaches? This comprehensive guide offers a detailed strategy for preventing and managing Secure Data Breaches. It covers essential topics like data privacy, security measures, and keeping customer trust intact.
Understanding the Landscape of Secure Data Breaches
As technology advances, data breaches are becoming a more common occurrence. Moreover, cybercriminals are constantly developing new ways to exploit weaknesses in corporate networks. These attacks vary widely, from sophisticated hacking attempts to insider threats and phishing scams. Consequently, understanding this evolving landscape is crucial for building a solid security strategy.
For example, the 2022 IBM Cost of a Data Breach Report reveals that the average global data breach costs companies $4.35 million. This cost rises to $9.44 million in the United States per incident. These staggering figures show the enormous financial and reputational damage caused by successful data breaches.
Common Breach Vectors: Cybercriminals use various methods to access sensitive data without authorization. These methods include malware, phishing, insider threats, and vulnerabilities in software or systems.
Emerging Threats: Besides these standard methods, new cybersecurity challenges are emerging. For instance, ransomware, cloud vulnerabilities, and advanced persistent threats (APTs) are becoming more prevalent. Organizations need to stay vigilant and be ready to tackle these evolving threats.
Industry Trends: Data breaches often target specific industries more frequently. For example, healthcare, finance, and retail sectors are commonly affected. Therefore, there is an urgent need for more robust security measures in these industries.
Implementing Robust Data Security Measures
Protecting customer data requires a multi-layered approach that combines cutting-edge technology, comprehensive policies, and employee training. Adequate data security involves both technical solutions and raising human awareness about cybersecurity.
| Technical Safeguards | Policy and Governance | Employee Awareness and Training |
| Implementing robust access controls, encryption, and regular software updates is crucial for reducing the risk of data breaches. Additionally, Security tools like firewalls, intrusion detection and prevention systems, and data loss prevention solutions are vital for protecting sensitive information. | Developing clear data privacy and security policies and having transparent governance structures ensures everyone knows their role in protecting customer data. Furthermore, regular audits and risk assessments help identify and fix vulnerabilities proactively. | Regular training sessions keep employees updated on the latest cybersecurity threats and best practices. By fostering a culture of vigilance and accountability, you ensure that everyone actively contributes to safeguarding customer data. |
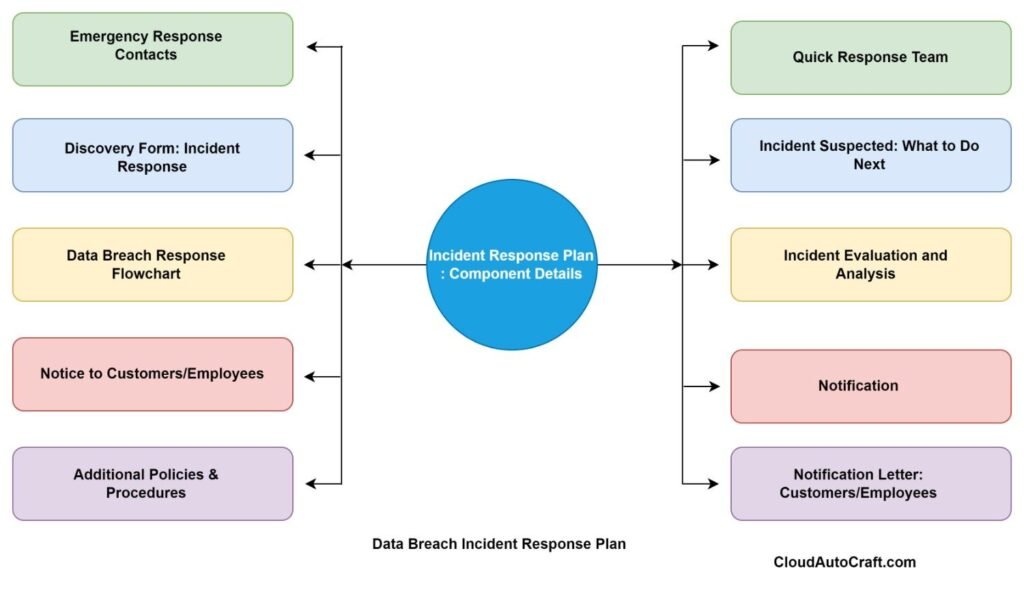
Preparing for the Inevitable: Secure Data Breaches Planning
Even with solid security measures in place, data breaches can still happen. Therefore, having a comprehensive incident response plan is crucial for minimizing the impact of a violation and rebuilding customer trust.
Incident Detection and Assessment:
First, clear protocols for detecting and quickly responding to potential data breaches should be set up. Additionally, real-time monitoring and alerting systems should be used to spot suspicious activity early. As a result, you can better assess the breach’s scope and severity.
Containment and Mitigation:
Next, take immediate steps to contain the breach and reduce its impact. Consequently, this includes isolating affected systems, blocking unauthorized access, and implementing emergency security measures. Additionally, work with cybersecurity experts and law enforcement for a thorough response.
Notification and Communication:
Finally, plan to notify affected customers, regulatory authorities, and other stakeholders. Specifically, craft transparent and empathetic communications that explain the incident, outline the resolution steps, and offer support to those affected. In addition, ensure your messaging is clear, concise, and sensitive to the impacts on individuals.
Click this video to learn about Process to Protect your Email and personal information:
Click here to Read more about Cyber Security – 2024
Restoring Trust and Rebuilding Reputation for Secure Data Breaches
A data breach can seriously harm a company’s reputation, damage customer trust, and lead to lasting financial and legal consequences. Therefore, restoring confidence and repairing the organization’s reputation is essential to move forward effectively.
| Transparent Communication: | Keeping communication open and honest with customers is crucial. Therefore, provide regular updates about the incident, the steps being taken to fix it, and how you’ll prevent future breaches. Then, Acknowledge the violation, show empathy, and firmly commit to protecting customer data. |
| Proactive Engagement: | Engage actively with customers, industry groups, and regulatory bodies. In addition, address their concerns and highlight your dedication to data privacy and security. Furthermore, contribute to industry efforts and collaborate with peers to share best practices. Ultimately, these actions strengthen the collective fight against data breaches. |
| Continuous Improvement: | After the incident, conduct a thorough review to find areas for improvement. Implement robust solutions and continuously update your data security protocols. Reassess and refine your incident response strategies and enhance employee training. This approach helps you stay ahead of evolving threats and maintain customer trust. |
| Safeguarding the Future: | After the incident, conduct a thorough review to identify areas for improvement. Then, implement robust solutions and continuously update your data security protocols. Additionally, reassess and refine your incident response strategies and enhance employee training. You can stay ahead of evolving threats and maintain customer trust by doing so. |
The Role of Leadership in Secure Data Breaches
Effective leadership is essential for handling data breach challenges and ensuring long-term security and resilience. Moreover, C-suite executives and board members play a crucial role in shaping the company’s data security strategy and promoting a culture of data stewardship.
 Strategic Vision: |  Risk Management: |  Security-Minded Culture |  Collaborative Approach |
| Effective leadership is critical to tackling data breach challenges and ensuring long-term security and resilience. Moreover, C-suite executives and board members play a crucial role in shaping the company’s data security strategy and promoting a culture of data stewardship. | First, leaders must craft a clear, long-term vision for data security. This vision should be in sync properly with the company’s strategic goals. It will guide development and implementation of security measures, policies, and governance structures. | Additionally, leaders should foster a culture of data stewardship. Instil a sense of responsibility for protecting every employee’s customer information. Invest in training and promote security best practices. Establish accountability mechanisms to ensure everyone follows the rules. | Finally, leaders must collaborate actively with industry peers, cybersecurity experts, and regulatory bodies. In addition, This helps them stay updated on emerging threats, share best practices, and contribute to developing effective data security solutions. |
Navigating the Legal and Regulatory for Secure Data Breaches
When data breaches happen, they create complex legal and regulatory challenges. As a result, organizations must handle these issues with care. They often find themselves tangled in data protection laws and regulations. Additionally, they face the legal and financial consequences of such breaches.
| Regulatory Compliance | Organizations must follow data protection regulations, such as GDPR in the EU, HIPAA in the US, and PIPEDA in Canada. Failing to comply can lead to significant fines and legal penalties. |
| Notification and Reporting Requirements | After a data breach, organizations must notify affected individuals, regulatory authorities, and other relevant stakeholders within a set timeframe. Neglecting these notification requirements can result in further legal and financial repercussions. |
| Liability and Lawsuits | Data breaches put organizations at risk of legal liabilities, including class-action lawsuits, regulatory investigations, and even criminal charges. Therefore, organizations must be prepared to manage these legal and financial risks to protect their business interests and reputation. |
Emerging Trends and Future Considerations of Secure Data Breaches
Navigating the Evolving Landscape of Data Security
The world of data security is constantly changing. New technologies, threats, and regulations keep emerging. Therefore, organizations must stay on their toes and proactively protect their data.
Advancements in Cybersecurity:
Governments worldwide are tightening data privacy regulations due to rising concerns. As a result, organizations must keep up with these changes. Staying informed allows them to adjust their data security practices, ensuring they meet regulatory requirements and reduce risks.
Evolving Regulatory Landscape:
With data privacy concerns growing, new regulations are being introduced, and existing ones are being strengthened. Moreover, this means organizations need to be updated on these changes. By doing so, they can adapt their security practices to remain compliant and safeguard their data.
Emerging Threats and Vulnerabilities:
New technologies like the Internet of Things (IoT) and cloud computing introduce fresh vulnerabilities. Cybercriminals are quick to exploit these weaknesses. Consequently, organizations must stay proactive and vigilant. This approach helps them address evolving threats and fortify their defences.
Secure Data Breaches: A Comprehensive Approach
Safeguarding Customer Data: A Crucial Responsibility for Multinational Enterprises
Protecting customer data is a top priority for global companies. Certainly, a data breach can severely affect the organization, its customers, and the wider business community. Therefore, a comprehensive, multi-layered approach to data security is essential to navigate these challenges. This strategy strengthens your defences, maintains customer trust, and fortifies the digital landscape.
Technical Safeguards:
Start by implementing solid technical measures. Furthermore, this includes encryption, access controls, and advanced security tools. Regularly update these safeguards to keep pace with evolving threats and new technologies. This proactive approach helps ensure your defences remain effective.
Policies and Governance:
Next, Make sure, that you put in place robust data privacy and security policies perfectly. Transparent governance structures are crucial so everyone understands their role in protecting customer information. Consistently you should perform audits and risk assessments to identify and resolve security gaps. Therefore, this ensures your policies stay relevant and practical.
Employee Awareness and Training:
Finally, focus on training your employees. Regular security awareness programs and a strong culture of data protection are essential. When vigilant and informed, employees act as an additional defence against potential breaches; this significantly reduces the risk of human errors that could lead to data breaches.
By integrating these elements, organizations can better safeguard customer data and build a more resilient security posture.
Incident Response and Reputation Management for Secure Data Breaches
Managing Data Breaches: A Comprehensive Approach
Data breaches can still happen even with the best security measures in place. Hence, maintaining an effective incident response plan is very much necessary. Equally important is a solid commitment to rebuilding customer trust. In the same way, you can minimize the breach’s impact and protect your organization’s reputation.
Strategic Preparation
- Incident Response Plan: Begin by crafting a detailed plan that defines roles, responsibilities, and escalation procedures. This ensures everyone knows their duties when a breach occurs.
- Ongoing Training: Regularly update your team with the latest threats and response techniques. This helps them stay prepared for evolving challenges.
- Security Measures: Invest in advanced security technologies such as firewalls, intrusion detection systems, and encryption. These tools are crucial for defending against potential breaches.
- Communication Protocols: Set up clear communication channels for internal and external notifications during a breach. Ensure you comply with regulatory requirements for disclosure.
Swift Detection and Diligent Response
- Timely Identification: Use sophisticated monitoring tools and threat intelligence to spot unusual activities quickly. Early detection is critical for managing a breach effectively.
- Containment Measures: Act quickly to isolate affected systems and prevent the breach from spreading. This limits the damage and protects other parts of your network.
- Investigation Procedure: Conduct a thorough investigation to understand the breach’s scope and methods. This insight helps address vulnerabilities and prevent future incidents.
Transparent Communication
- Stakeholder Updates: Provide clear and timely updates to all stakeholders about the breach. Keeping everyone informed helps maintain trust.
- Honesty and Forthrightness: Be honest and direct in your communications. Transparency fosters trust and credibility during uncertain times.
- Regulatory Compliance: Adhere to disclosure regulations to reinforce your organization’s integrity and commitment to compliance.
Holistic Recovery and Reputational Restoration
- Operational Normalcy: Focus on restoring normal operations while enhancing security measures to prevent future breaches. This helps you get back on track.
- Reputation Damage Assessment: Evaluate the impact on your reputation by analyzing media coverage and public sentiment. Understanding the damage helps in addressing it effectively.
- Proactive Engagement: Engage with stakeholders proactively. Show genuine regret and a strong commitment to improving security. This effort helps in rebuilding your reputation.
By following these steps, organizations can manage the fallout from data breaches more effectively and work towards restoring their reputation and trust.
Conclusion: A Call to Action

Addressing Data Breaches: A Collaborative Approach
Data breaches are significant issues for large companies. Indeed, they risk exposing millions of customers’ personal information and eroding trust. To combat this, companies need to take several key steps. First, they should invest in the latest technology. Next, they need to establish firm policies. Additionally, promoting data security awareness among all employees is crucial. However, safeguarding data isn’t a solo effort. It requires collaboration. Therefore, companies should work with peers, cybersecurity experts, and government officials. By joining forces, they can create more robust strategies to prevent data breaches and enhance internet security.
Time is critical. Thus, companies must act swiftly and work together to protect data effectively. This proactive approach helps keep customers safe, preserves the company’s reputation, and contributes to a safer online environment for everyone.
Click here to Read more about Cloud-Security – 2024 && DevOps-Security – 2024
FAQs:
What are the most common vulnerabilities that cybercriminals exploit to initiate Secure Data Breaches?
Answer: Cybercriminals often target vulnerabilities in outdated software, unpatched security flaws, weak passwords, and lax access controls. They also use tactics like phishing emails and pretexting to trick you into revealing sensitive information or granting unauthorized access.
What legal implications do data breaches have, and how can businesses navigate them?
Answer: When it comes to the law, we’ve got to be careful! Information breaks can prompt fines and claims. we should work with legal experts to understand our responsibilities and take the right steps.
How can businesses take to detect and respond to insider threats that may lead to data breaches?
Answer: We can address insider threats by training employees on cybersecurity best practices. We should also watch for signs of suspicious behavior. Implement role-based access controls and monitor user activities for anomalies. However, Let’s create a culture of transparency and accountability. Meanwhile, encourage employees to report potential threats promptly to strengthen our defenses.
What immediate steps should a business take after a data breach to protect sensitive information?
Answer: If a breach happens, we need to act fast! First, we should isolate the affected systems. Then, we must notify customers and authorities while we work on fixing the problem.
Originally posted 2024-05-12 06:58:10.


15 thoughts on “How to Respond to Secure Data Breaches: Best Practices”