In today’s ever-changing digital world, traditional perimeter-based security models no longer cut it. Therefore, This is where Zero Trust Architecture (ZTA) comes in, providing a more robust and flexible security approach. It can be smoothly integrated into your DevOps workflows. This guide will explore how you can embrace zero-trust principles to boost the security of your DevOps processes and protect your critical assets.
Content:
- Understand Zero Trust Architecture
- Aligning Zero Trust Architecture with DevOps
- Implementing Zero Trust Architecture in DevOps
- Leveraging DevSecOps for Zero Trust Architecture
- Securing the Software Supply Chain
- Embrace Cloud-Native Security with Zero Trust Architecture
- The Role of Automation and Orchestration
- Implement Continuous Monitoring and Incident Response
- Fostering a Culture of Security
- Real-World Example: Securing a CI/CD Pipeline
- Overcoming Challenges
- Conclusion
- FAQs:
Understand Zero Trust Architecture
To scale efficiently, start with the Horizontal Pod Autoscaler (HPA). It adjusts the number of pods based on CPU, memory usage, or custom metrics. Next, use the Vertical Pod Autoscaler (VPA) to adjust resource requests and limits dynamically.
Additionally, implement the Cluster Autoscaler to add or remove nodes depending on workload demands. Moreover, resource quotas should be set up to ensure resources are fairly distributed among different teams and applications.
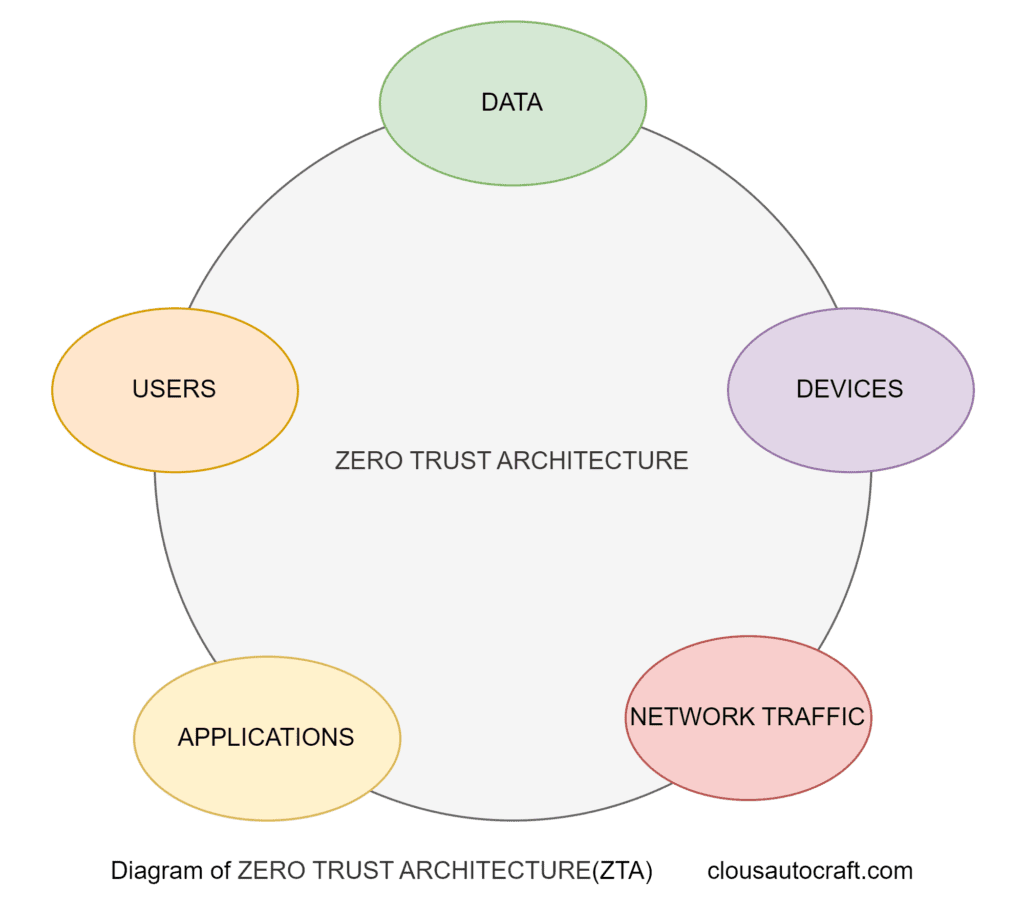
Aligning Zero Trust Architecture with DevOps
Integrating Zero Trust principles into your DevOps workflows is critical for a strong security stance. DevOps focuses on the fast delivery of software and services, which can sometimes clash with traditional security practices.
However, adopting a Zero Trust approach helps you balance agility and security. This way, your DevOps processes stay efficient while protecting your systems and data.
Implementing Zero Trust Architecture in DevOps
| Identity and Access Management | We ensure that all users, devices, and applications are authenticated and authorized before they access any resources. This means using multi-factor authentication (MFA), granting just-in-time access, and implementing role-based access controls (RBAC) to follow the principle of least privilege. Regularly reviewing and updating IAM policies is crucial to keeping up with evolving threats and changes in the DevOps environment. |
| Continuous Verification | Continuously monitor and check the security of your DevOps environment. Focus on your code’s integrity, assess your infrastructure’s health, and monitor user and application behaviour. |
| Automated Remediation | Use automation and orchestration tools to detect and respond to security incidents quickly. However, This minimizes potential impacts and speeds up recovery. |
Leveraging DevSecOps for Zero Trust Architecture
DevSecOps, which integrates security practices into the DevOps workflow, is essential for implementing Zero Trust in your organization. Adding security controls and testing into your continuous integration and delivery (CI/CD) pipeline makes security a crucial part of your DevOps processes.
This approach ensures that security isn’t an afterthought. Instead, it helps identify and address vulnerabilities early in the development lifecycle. As a result, you reduce the risk of security breaches and avoid issues down the line.
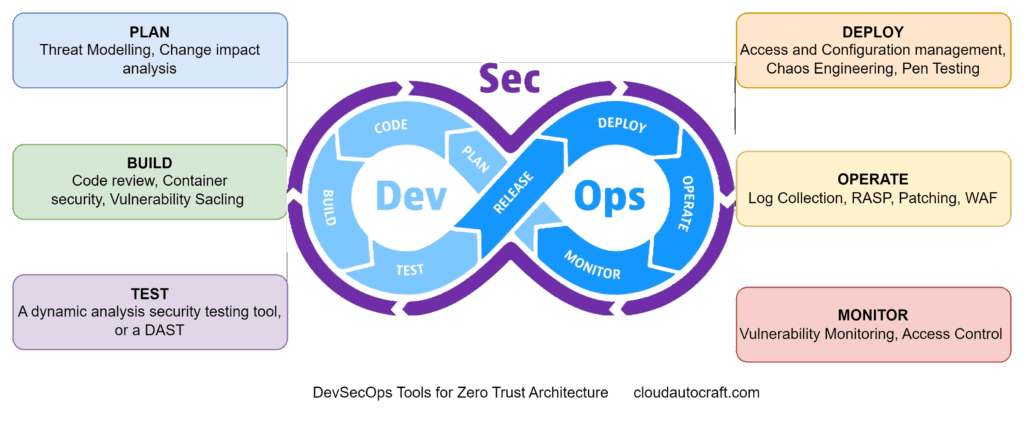
Securing the Software Supply Chain
When it comes to Zero Trust and DevOps, securing the software supply chain is crucial. Malicious actors might target your systems through compromised third-party libraries, open-source components, or your build pipeline.
To address this, strong supply chain security measures must be implemented. For instance, use code scanning, manage dependencies carefully, and validate your build process. This way, you ensure that every part of your software is trustworthy and free from known vulnerabilities.

Embrace Cloud-Native Security with Zero Trust Architecture
As you move to cloud-based DevOps, adopt cloud-native security solutions that fit smoothly with your cloud infrastructure and platforms. Use cloud-based identity providers, managed firewalls, and distributed denial-of-service (DDoS) protection services to strengthen your Zero Trust approach.
These cloud-native tools offer scalable, flexible, and cost-effective security solutions. Consequently, they are well-suited to the dynamic nature of your DevOps environment.
The Role of Automation and Orchestration
Automation and orchestration are vital in implementing and maintaining a successful Zero Trust architecture in your DevOps environment. Therefore, automate security controls, policy enforcement, and incident response to ensure everything runs smoothly, scales effectively, and responds quickly.
Additionally, integrating security into your DevOps toolchain reduces manual effort. This minimizes human error and helps you respond to threats more efficiently.
Implement Continuous Monitoring and Incident Response
Continuous monitoring and incident response are crucial for a robust Zero Trust architecture. Therefore, real-time monitoring and alerts should be set up to detect and address security incidents quickly.
Additionally, review and test your incident response plans regularly. Hence, this helps ensure your team is ready to handle various security events, from unauthorized access attempts to data breaches.
Fostering a Culture of Security
Embracing Zero Trust in DevOps is more than a technical challenge; it also involves a cultural shift within your organization. Therefore, encourage your DevOps and security teams to work together and ensure security is seen as a shared responsibility.
Additionally, offer regular training and awareness programs to educate your employees about Zero Trust principles. By fostering a security-conscious mindset, you empower your team to make informed decisions, strengthening the overall security of your DevOps environment.
Real-World Example: Securing a CI/CD Pipeline
Let’s look at how to apply Zero Trust principles to secure a CI/CD pipeline in a DevOps environment. Imagine a company that develops and deploys web applications using a CI/CD pipeline. To implement Zero Trust, we might:
- Multi-factor authentication is required for all developers and operators accessing the pipeline.
- Continuously monitor the pipeline for any suspicious activities or unauthorized changes to the codebase.
- Automate security checks, such as code scanning and dependency analysis, as part of the build process.
- Restrict access to production environments until the integrity of the deployed application has been verified.
By adopting these Zero Trust practices, we can enhance the overall security of our CI/CD pipeline and reduce the risk of security breaches that could compromise our software deliveries.
Check this below video, Get more insight into Zero Trust Architecture – Real World Example
Overcoming Challenges
Implementing Zero Trust in a DevOps environment can come with some challenges, such as:
- Integrating security controls without slowing down DevOps agility and efficiency.
- Ensuring smooth collaboration between DevOps and security teams.
- Adapting existing processes and tools to fit Zero Trust principles.
- Balancing security with user experience.
To tackle these challenges, we need a flexible and iterative approach. Moreover, regularly evaluating your Zero Trust implementation is crucial. Building a strong security culture within your organization can help you address these challenges effectively.
Conclusion
Embracing Zero Trust in your DevOps workflows is a crucial step for boosting the security and resilience of your digital infrastructure. Aligning your DevOps practices with Zero Trust principles builds a more robust and adaptable security posture. Additionally, this approach helps reduce the risk of security breaches and keeps your software deliveries secure.
Remember, transitioning to Zero Trust is an ongoing journey. Therefore, it’s essential to keep improving your security measures. Furthermore, creating a security-conscious culture within your organization is critical. Hence, this will help you avoid evolving threats and protect your organization’s valuable assets.
Click here to Read more about Cloud-Security – 2024 && Cyber Security – 2024
FAQs:
What are the key principles of Zero Trust Architecture in Secure DevOps?
Answer: Securing your DevOps environment starts with a solid grasp of Zero Trust Architecture (ZTA) principles. ZTA follows the mantra, “Never trust, always verify.” However, this means every access request is carefully checked before being approved. Additionally, the principle of least privilege ensures users and applications have only the minimal access they need. Moreover, continuous monitoring keeps a close eye on all activities. Integrating these principles into your DevOps setup can significantly enhance your security.
How can micro-segmentation improve security in a DevOps pipeline?
Answer: Micro-segmentation can significantly boost security in your DevOps pipeline by breaking your network into smaller, isolated segments. Consequently, attackers can’t quickly spread to other areas if one segment is breached. It’s like having internal firewalls that reduce the attack surface. Implementing micro-segmentation with the right tools and techniques enhances overall security and allows for more detailed control over network traffic and access.
What are the challenges of implementing Zero Trust in a CI/CD pipeline?
Answer: Implementing Zero Trust in a CI/CD pipeline can be challenging, as it means keeping security tight without slowing down development. Constantly verifying access requests can be a bit cumbersome. However, you can smoothly integrate Zero Trust principles while boosting security by using a strategic approach, leveraging automation, and making small, incremental changes.
How do identity and access management (IAM) practices integrate with Zero Trust in DevOps?
Answer: Identity and access management (IAM) practices fit perfectly with Zero Trust in DevOps by ensuring every access request is authenticated and authorized. Multi-factor authentication (MFA) and role-based access control (RBAC) enforce strict access rules. Additionally, continuous identity verification aligns well with Zero Trust principles. This integration boosts security by reducing the risk of unauthorized access within your DevOps workflows.
Originally posted 2024-06-07 16:02:54.

3 thoughts on “How to Secure DevOps with Zero Trust Architecture”