In today’s digital world, cloud computing is a key player for businesses of all sizes, offering flexibility, scalability, and cost-efficiency. However, these benefits also come with serious security challenges. Therefore, understanding cloud computing security architecture is crucial for protecting your data and maintaining your clients’ trust. In this blog, we’ll dive into the essential components, best practices, and tools you need to secure your cloud environment.
Content
- What is Cloud Computing Security Architecture?
- Why is Cloud Computing Security Architecture So Important?
- Key Components of Cloud Computing Security Architecture
- Best Practices for Cloud Computing Security
- Technical Solutions for Cloud Computing Security Architecture
- Common Challenges in Cloud Computing Security Architecture
- How to Address Cloud Computing Security Architecture Challenges
- Tools and Technologies for Cloud Security
- Conclusion: Cloud Computing Security Architecture
- FAQs:
What is Cloud Computing Security Architecture?
Cloud computing security architecture is like a well-organized plan that combines policies, technologies, and controls to keep your systems, data, and applications safe in the cloud. It includes various layers of security, such as encrypting data and managing who has access. As a result, all these measures work together to ensure your sensitive information remains protected from threats.
Why is Cloud Computing Security Architecture So Important?
Imagine if your sensitive customer data or intellectual property ended up in the wrong hands; the fallout could be huge—both financially and for your reputation. That’s why securing the cloud is crucial::
- Protecting Your Data: Cloud systems often store a lot of valuable information. Without solid security, this data becomes vulnerable to theft or compromise.
- Staying Compliant: Additionally, regulations like GDPR (General Data Protection Regulation) and HIPAA (Health Insurance Portability and Accountability Act) impose strict rules for protecting data. Therefore, if you don’t follow these rules, you could face hefty fines and legal trouble.
- Keeping Your Business Running: Moreover, cyberattacks can disrupt your operations. As a result, a strong security setup helps minimize downtime and ensures your business continues running smoothly.
- Maintaining Customer Trust: Lastly, security breaches can damage trust. Since customers expect their data to be safe, ensuring a secure cloud environment helps you keep that trust intact.
Key Components of Cloud Computing Security Architecture
Building a robust cloud security architecture involves several components, each playing a crucial role. To understand this better, let’s break down these components:
Identity and Access Management (IAM)
Think of IAM as the system that decides who gets access to what in your cloud setup. It’s somewhat like handing out keys to different rooms in your house.
To manage access efficiently, take these steps properly:
- User Authentication: This is about making sure the right people get in. Just using passwords isn’t enough anymore, so it’s smart to use multi-factor authentication (MFA) for extra security.
- Role-Based Access Control (RBAC): Not everyone requires access to every resource.. Assign permissions based on roles, so people only get access to what they actually need.
- MFA (Multi-Factor Authentication): Ask users to prove their identity in more than one way. For example, they might need to enter a password and then provide a code sent to their phone.
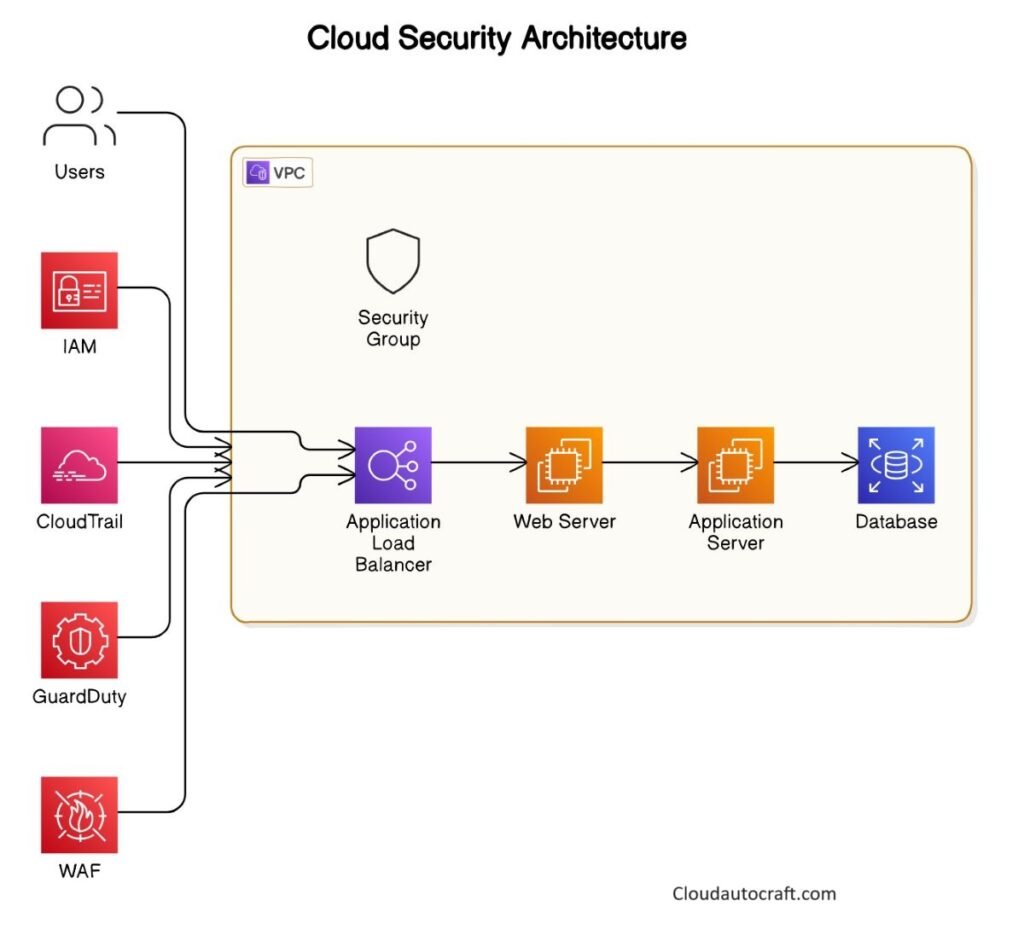
Data Encryption
Think of encryption as a secret code for your data. It ensures that even if someone manages to access your information without permission, they still can’t read it without the right decryption key. We can classify encryption into two major categories:
- Data at Rest Encryption: This type protects data stored on physical or virtual disks in the cloud. For this purpose, use encryption tools from your cloud provider, such as AWS Key Management Service (KMS).
- Data in Transit Encryption: On the other hand, this type keeps data safe as it travels between users, devices, and cloud services. So, To ensure secure transmission, utilize protocols like HTTPS and SSL/TLS.
Network Security
Think of your network as the highway for data in the cloud, and you want to make sure it’s secure with no gaps. To achieve these objectives, you should consider the following strategies:
- Firewalls: These act as security guards standing between your cloud resources and potential threats. Therefore, you should set up cloud-native firewalls to filter and control the traffic going in and out.
- Virtual Private Network (VPN): Additionally, a VPN creates a secure tunnel for your data as it travels. Consequently, it keeps your information safe from anyone trying to eavesdrop.
- Intrusion Detection and Prevention Systems (IDPS): Furthermore, these systems monitor network traffic for any unusual or malicious activity. As a result, they can act to block breaches before they occur.
Endpoint Security
Endpoints such as laptops, smartphones, and IoT devices can be gateways for cyber threats. To keep them secure, consider these practices:
- Antivirus and Anti-Malware Software: First, regularly update and run security software on all your devices. Consequently, this helps detect and block any potential threats effectively.
- Device Management: Additionally, use Mobile Device Management (MDM) tools to set security policies. For instance, require strong passwords and enable encryption on devices.
Application Security
Applications running in the cloud must be secure from the ground up. To achieve this, follow these steps:
- Regular Security Testing: First, vulnerability assessments and penetration testing must be conducted to identify and fix security holes.
- Secure Development Lifecycle (SDLC): Additionally, incorporate security practices at every stage of application development, from design to deployment.
- Web Application Firewalls (WAF): Finally, WAFs are used to protect applications from common attacks such as SQL injection and cross-site scripting (XSS).
Best Practices for Cloud Computing Security
Now that we’ve covered the components, let’s dive into some best practices. These strategies are tried-and-true ways to keep your cloud environment secure:
1. Implement a Shared Responsibility Model
In the cloud, security is a team effort between you and your cloud provider. Therefore, it’s crucial to understand what each party is responsible for. Typically, the provider handles the security of the cloud infrastructure, while you are responsible for securing your data and applications within the cloud.
2. Regularly Update and Patch Systems
Keeping your software up to date is essential. Since cyber attackers often exploit vulnerabilities in outdated software, it’s crucial to make it a habit to regularly update and patch your cloud services, applications, and operating systems. By doing so, you can fix any security flaws and stay protected.
3. Enable Logging and Monitoring
Logging and monitoring provide a clear view of what’s happening in your cloud environment. Therefore, tools like AWS CloudTrail or Azure Monitor can be used to keep track of activities, spot any unusual behaviour, and quickly address potential threats.
4. Backup Data Regularly
Data can be lost due to cyber-attacks, accidental deletions, or system failures. To protect against these risks, ensure you back up your data regularly. By doing so, you can quickly restore it and minimize downtime. Additionally, automating backups helps prevent human error.
5. Conduct Regular Security Audits
Regular security audits are essential for maintaining the safety of your cloud environment. They help you identify weaknesses, verify that you’re following security policies, and make any necessary improvements. Consequently, audits keep you proactive in managing security risks.
Technical Solutions for Cloud Computing Security Architecture
Let’s explore some technical solutions to boost your cloud security:
Using IAM Policies in AWS
AWS Identity and Access Management (IAM) helps you manage who can access your AWS services and resources. For instance, you can use IAM policies to control permissions. Here’s an example of an IAM policy that gives read-only access to an S3 bucket:
JSON Code:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::your-bucket-name",
"arn:aws:s3:::your-bucket-name/*"
]
}
]
}This policy ensures that users can only view the content of the specified S3 bucket without being able to make any changes.
Configuring Network Security Groups in Azure
Azure Network Security Groups (NSGs) help you manage network traffic to and from your Azure resources. To set up an NSG, follow these steps:
- Allow HTTP Traffic: Start by creating an inbound rule for port 80.
- Allow HTTPS Traffic: Next, create an inbound rule for port 443.
- Deny All Other Traffic: Finally, set a default rule to block all other inbound traffic, which helps reduce your exposure.
Common Challenges in Cloud Computing Security Architecture
Even with the best security measures in place, challenges remain. Here are some common cloud security challenges:
- Data Breaches: When sensitive data is stored in the cloud, it becomes a potential target for cyber threats. Therefore, implement strong encryption and access controls to protect data.
- Misconfiguration: Misconfigured cloud services can leave security gaps. Thus, use automated tools to scan for and correct misconfigurations.
- Insider Threats: Employees or contractors with malicious intent can misuse their access privileges. Consequently, implement strict access controls and monitor user activity to detect suspicious behavior.
- Compliance Issues: Different industries have different regulatory requirements. Therefore, use compliance management tools provided by your cloud provider to ensure you meet these standards.
How to Address Cloud Computing Security Architecture Challenges
- Use Automated Security Tools: Automate the detection and fixing of misconfigurations with tools like AWS Config or Azure Security Center. By doing so, you can keep everything secure more easily without having to check every detail manually.
- Train Employees: Regular security training is crucial for helping employees spot and avoid security risks. For instance, teach them about phishing scams, how to use strong passwords, and why protecting data is important.
- Enforce Least Privilege Access: Provide users with only the access they need to perform their jobs. This approach helps minimize the risk of insider threats by limiting what each person can see and do.
- Leverage Compliance Tools: Utilize tools like AWS Artifact or Azure Compliance Manager to handle compliance documentation and audit reports. Consequently, these tools help you stay on top of regulatory requirements and maintain your security posture.
Tools and Technologies for Cloud Security
Here are some recommended tools to enhance your cloud security:
| Tool | Purpose |
|---|---|
| AWS Identity and Access Management | Manage user permissions |
| Azure Security Center | Monitor security across Azure services |
| Cloudflare | Web application firewall |
| Splunk | Security information and event management |
Conclusion: Cloud Computing Security Architecture
In conclusion, Securing your cloud environment goes beyond just technology; it’s about building a culture of security awareness. By understanding cloud security architecture, following best practices, and using the right tools, you can protect your data, stay compliant, and fend off cyber threats.
To maintain security, make sure to regularly update your security measures, keep your team trained, and stay up-to-date with the latest security trends. Remember, security isn’t a one-time task; instead, it’s an ongoing process.
Click here for more insights on various Cloud-Security && Cyber Security topics.
FAQs:
What is the biggest challenge in Cloud Computing Security Architecture?
Answer: One of the biggest challenges is often misconfiguration. Since cloud services can be quite complex, incorrect settings can inadvertently open up security vulnerabilities. Therefore, using automated tools to spot and fix these misconfigurations can greatly reduce this risk.
How does encryption help in cloud security?
Answer: Encryption converts your data into a coded format that is unreadable without the correct decryption key. It’s essential for protecting data both at rest (stored data) and in transit (data being transmitted). Even if unauthorized users access the data, they can’t read it without the encryption key.
What are the common security threats in cloud computing?
Answer: Cloud computing has several security risks. Data breaches, insider threats, and account hijacking are common. Misconfigured settings can expose your data, while denial-of-service attacks can disrupt your services. Ensure APIs are secure, data loss is minimized, and your cloud provider’s security controls are effective. Also, stay aware of compliance and legal issues to keep your data safe.
Why is multi-factor authentication (MFA) important?
Answer: Multi-factor authentication (MFA) is essential because it adds an extra layer of security beyond just a password. With MFA, you need two or more verification methods—such as a password and a code sent to your phone. This approach makes it much harder for unauthorized users to access your accounts. Even if someone manages to steal your password, they will still need that second factaor to gain access. Consequently, MFA greatly lowers the risk of account breaches and boosts overall security.
Originally posted 2024-08-29 13:03:56.

