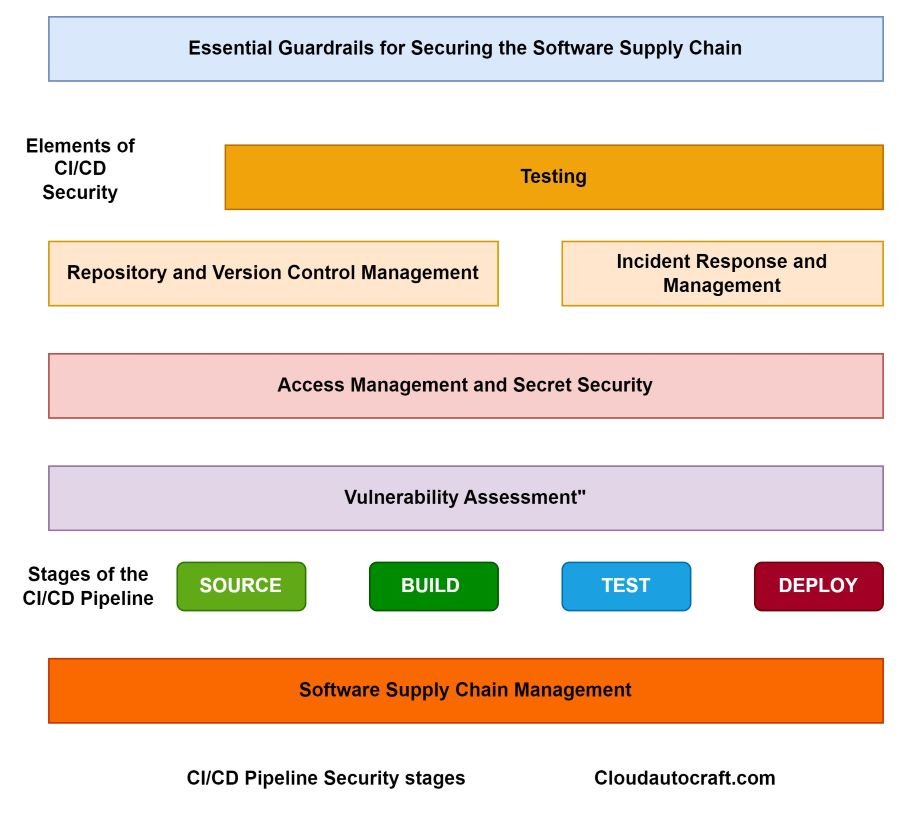
In today’s software world, CI/CD pipeline security is essential for quickly delivering apps. But we sometimes forget about security. This guide discusses the best ways to maintain CI CD pipeline security. We’ll cover how to stop bugs, keep your secrets safe, and follow all the rules. Additionally, we’ll share tips on monitoring, access control, and best practices to ensure your pipeline is efficient and secure. Stay ahead of threats and keep your development process smooth and safe.
Content:
- Why is CI/CD Pipeline Security Important?
- Secure Repositories for CI/CD Pipeline Security
- CI/CD Pipeline Security in Build
- CI/CD Pipeline Security in Deployment
- Secure Infrastructure for CI/CD Pipeline Security
- Implement Strong Authentication and Authorization
- Secure Credentials
- Automate Testing & Code Review
- Secure Network for CI CD Pipeline Security
- Implement Monitoring and Logging
- Automated CI/CD Pipeline Security Updates
- Real-World Example: A Bank's CI/CD Pipeline Security
- Shift-Left CI/CD Pipeline Security
- Collaboration for CI CD Pipeline Security
- Conclusion
- FAQs:
- How can I ensure the CI/CD pipeline security of third-party integrations?
- How can I effectively manage CI CD pipeline security updates and patches?
- What steps should I take to align automation with security requirements in my pipeline?
- How do I address security risks with containerization and orchestration in the CI/CD process?
Why is CI/CD Pipeline Security Important?
Before we get into the nitty-gritty of security practices, it’s essential to know where your CI/CD pipeline might be vulnerable to attacks. Consider all the ways someone could sneak in—like the tools you use, your setup, and every step of your pipeline.
By gaining this understanding, you can better prioritize your security efforts. Consequently, you can focus on the areas most vulnerable to attack. This initial step is essential for building a robust security strategy.
Secure Repositories for CI/CD Pipeline Security
Your code repository is like the backbone of your CI/CD pipeline. Furthermore, It’s super important to keep it safe from hackers and other problems. Here are a few key things to do:
- Implement strong access controls and authentication.
- Use version control systems with built-in security features.
- Scan your code for vulnerabilities regularly.
- Regularly review and update your security policies.
When you do these things, your code stays safe and sound while working on it.
CI/CD Pipeline Security in Build
The built environment is where your code gets put together, tested, and prepared for use. It’s super important in your CI/CD setup, but it can also be a target for bad guys. So, here are a few things to keep in our mind:
- Use separate build environments to keep different codes and tools apart.
- Control who can get into the build system tightly.
- Use safe containers to keep your build stuff separate and more challenging to attack.
When you do these things, your builds stay safe and work as they should.
CI/CD Pipeline Security in Deployment
Once your code is ready to go live, you must deploy it correctly. Certainly, This includes setting up everything, like managing configurations, installing the app, and getting the infrastructure ready. Each of these steps has its security challenges. Here’s what to do:
- Use tools that automatically deploy your stuff safely and track what’s happening.
- Set up systems that watch for any security problems and tell you right away.
- Keep checking how you deploy things and what security settings you must find to fix any weak spots.
When you take care of your deployment like this, you lower the chances of any security problems and make sure your apps go live smoothly.
Secure Infrastructure for CI/CD Pipeline Security
The infrastructure supporting your CI/CD pipeline plays a significant role in its security. Certainly, This includes all your servers, networks, and cloud services. So, make sure to follow these essential steps:
- Pick cloud providers with robust security features like encryption and access controls.
- Keep everything updated with the latest security fixes.
- Set up systems to watch for security issues and quickly inform you.
- Check your security settings regularly to find and fix any problems.
Nevertheless, When you focus on securing your infrastructure like this, you build a strong base for your CI/CD setup and lower the chances of attacks.
Implement Strong Authentication and Authorization
Having strong authentication and authorization is key to keeping your CI/CD pipeline safe. Here’s why:
Moreover, when you use these practices, you ensure that only the right people can get into your CI/CD system and see important stuff.
Secure Credentials
Secrets like API keys and passwords are essential for your CI/CD pipeline to work correctly. Likewise, Here’s how to keep them safe:
- Implement special tools to handle secrets securely.
- Always use encryption to protect secrets, even when stored or moving around.
- Make sure only the right people and things can get to secrets by limiting access.
- Keep an eye on who’s using secrets and watch out for anything weird happening.
Moreover, Doing these things makes it harder for anyone to mess with your secrets and keeps your pipeline safe.
Automate Testing & Code Review
Automating security testing in your CI/CD pipeline is crucial in a fast-moving development setup. Consequently, This helps catch problems early on. Here’s how:
- Use tools that check your code while it’s being built to find security issues.
- After your apps are live, use tools that keep scanning for problems (DAST).
- Use tools that check your code before it’s built to spot security problems (SAST).
- Test your systems like a hacker would to find problems (penetration testing).
- Always have other developers check your code to find mistakes and make it safer.
Nevertheless, When you do these things, your code gets checked out well and stays safe when it’s out there.
Secure Network for CI CD Pipeline Security
Ensuring the security of your CI/CD pipeline depends on the network that links all its parts. Therefore, here’s what to do to keep it safe:
- Use firewalls to block anyone who shouldn’t get into your CI/CD stuff.
- Divide your network into parts to separate essential things and stop attacks from spreading.
- Use systems that spot lousy stuff happening on your network and stop it (IDS/IPS).
- Keep checking your network setup to find and fix any weak spots.
Moreover, When you do these things, it’s harder for anyone to mess with your CI/CD setup and try to break in.
Implement Monitoring and Logging
Continuous monitoring and logging are crucial for effectively identifying and responding to security incidents. So, Here’s how to implement them:
- To begin with, security monitoring tools should be used to track user activity, system events, and security alerts. Eventually, this helps stay vigilant about potential threats.
- Next, configure logging to capture all relevant events and actions within your CI/CD pipeline. However, This ensures you have a detailed record of what’s happening.
- Additionally, security information and event management (SIEM) solutions can be implemented to aggregate and analyze security data from multiple sources. Moreover, This centralizes your security monitoring efforts.
- Furthermore, alerts and notifications should be created to inform the security team about potential incidents promptly. This enables quick response to any security threats detected.
By implementing these practices, you can gain valuable insights into your CI/CD pipeline’s security posture and effectively detect and respond to threats.
Click this video to learn about CI/CD Pipeline Security
Automated CI/CD Pipeline Security Updates
Just like you wouldn’t drive a car with old tires or brakes, you must keep your CI CD Pipeline Security current. Make sure you have a way to automatically install security fixes and updates for your software and setup. Moreover, This keeps everything running on your tools’ newest and safest versions.
Real-World Example: A Bank’s CI/CD Pipeline Security
Imagine you’re a bank using a CI/CD pipeline to launch your mobile banking app. Security is a top priority because we handle sensitive customer data. Here’s how we ensure our pipeline stays secure:
- Firstly, everyone needs more than just a password to get in—we use multi-factor authentication. Additionally, This adds an extra layer of security.
- Secondly, our servers are kept safe in a private cloud, where only authorized people can access them. Undoubtedly, This ensures our infrastructure is protected.
- Additionally, our dedicated team regularly checks for weaknesses and tries to break in through vulnerability scanning and penetration testing. This proactive approach helps us find and fix potential issues before they become problems.
- Furthermore, we’ve set up a system to update our security automatically. So, this means we’re always protected by the latest defenses against threats.
With these measures, we ensure our CI/CD Pipeline Security is vital and safeguard our customers’ sensitive information.
Shift-Left CI/CD Pipeline Security
Shift-left security is about building security into your process from the very start. So, It’s like making a car with safety features already included instead of adding them later as an afterthought.
You put it right from the beginning rather than waiting until the end to add security. Therefore, this helps reduce the risk of problems or vulnerabilities popping up down the line.
Essentially, it’s about making security a priority from the get-go. In the same way, you have a safer, more reliable final product. Overall, It’s all about being proactive and thoughtful about security throughout the process.
Collaboration for CI CD Pipeline Security
| Teamwork: | Securing our CI/CD pipeline requires collaboration among developers, security experts, and operations teams. It’s like a team of engineers building a vital highway together, each contributing their expertise to create a safe infrastructure. |
| Open Communication: | Like sharing plans on a highway project, open communication and knowledge sharing are crucial for CI/CD pipeline security. It’s about sharing tips, lessons, and ideas to make our pipeline safer and more reliable. |
| Regular Security Audits: | Regular security checks are essential. They help us find areas to improve, such as regular inspections on a highway to keep it safe and well-maintained. |
| Continuous Improvement: | CI CD pipeline security is an ongoing journey. We should always learn and improve based on new risks and best practices. It’s like constantly upgrading and enhancing our highway to ensure it stays safe and resilient. |
Conclusion
Securing our CI/CD pipeline safeguards our software and business. Also, It involves understanding potential vulnerabilities in code repositories, build and deployment environments, and network security, then applying best practices to address them. So, Continuous monitoring and logging are vital for detecting and responding to threats promptly.
Therefore, we establish a secure and dependable CI/CD pipeline that delivers safe software releases by implementing these measures. It’s about proactively identifying and mitigating risks throughout the development and deployment phases.
Click here to Read more about Cloud-Security – 2024 && Cyber Security – 2024
FAQs:
How can I ensure the CI/CD pipeline security of third-party integrations?
Answer: Securing third-party integrations is crucial. We carefully review vendors, check their security practices, and watch for vulnerabilities or breaches. We also enforce strict access controls and regularly update integrations to reduce risks.
How can I effectively manage CI CD pipeline security updates and patches?
Answer: Effectively managing security updates and patches entails automating the swift deployment of deployments. Moreover, We also regularly check for vulnerabilities and prioritize critical updates for immediate action. Continuous monitoring helps us find and fix security issues promptly.
What steps should I take to align automation with security requirements in my pipeline?
Answer: To integrate automation with security in your pipeline, start by adding security checks early. Automate testing and enforce policies as code. So, Keep monitoring constantly and update dependencies regularly. Also, ensure strict access controls and train your team in security best practices.
How do I address security risks with containerization and orchestration in the CI/CD process?
Answer: Dealing with security risks in containerization and orchestration tools involves taking proactive steps. Before deployment, we scan container images for vulnerabilities and use runtime security tools to monitor and protect against threats while containers run. Therefore, Keeping container images and orchestration platforms updated with patches reduces security risks.
Originally posted 2024-06-16 16:00:36.


4 thoughts on “CI/CD Pipeline Security: What Are the Best Practices”