Content:
- Introduction: Docker Security Vulnerabilities
- 1. Docker Updates: Your First Line of Defence
- 2. Docker Security Vulnerabilities: Don’t Trust Every Image You Pull
- 3. Avoid Docker Security Vulnerabilities by Ditching Root Access
- 4. Turn on Docker Content Trust (DCT)
- 5. Secure Your Software Supply Chain
- 6. Scan Your Images — Always
- 7. Isolate Containers with Network Segmentation
- 8. Protect Containers in Runtime
- 9. Don’t Store Secrets in Containers
- 10. Harden the Docker Host Itself
- Architecture: Secure Docker Deployment
- Conclusion: Docker Security Vulnerabilities
- FAQs:
Introduction: Docker Security Vulnerabilities
In today’s rapidly evolving tech landscape, Docker has become the go-to tool for containerization. It helps developers build, ship, and run applications faster. However, as Docker adoption grows, so do the security concerns around it. So, if you’re relying on containers, it’s crucial to address Docker Security Vulnerabilities before they become real threats.
At this point, you’re probably asking yourself, “How can I lock down my Docker setup?”
You’re definitely where you need to be!”. Here, we’ll walk you through the very best and most up-to-date strategies to crush Docker security pitfalls.
1. Docker Updates: Your First Line of Defence
First off, Docker keeps rolling out updates to patch bugs and close security holes. Consequently, if you skip those updates, you’re basically leaving your engine wide open for attackers. Moreover, staying current not only fixes known issues but also brings in new security enhancements. Therefore, make it a habit to update Docker as soon as new releases drop.
What You Should Do:
- Always check the official Docker blog for updates.
- Automate Docker engine updates using CI/CD tools like Jenkins or GitHub Actions.
- Also, monitor Docker CVEs through trusted sources like NVD.
Real Example: In fact, back in early 2025, a critical flaw popped up in the runc component. Consequently, teams who jumped on updates right away stayed protected. On the other hand, those who hesitated? Well, they found themselves scrambling to plug the holes. Ultimately, this incident underscores why keeping Docker current is non-negotiable.
2. Docker Security Vulnerabilities: Don’t Trust Every Image You Pull
You might think that all Docker images are safe — but that’s far from true. In reality, images from unknown sources might contain hidden malware.
Here’s What You Can Do:
- Always prefer images from Docker’s official library.
- Go for minimal images like
alpineordistrolessto reduce attack surfaces. - Scan third-party images before use.
Tip: Lighter images not only reduce vulnerabilities but also improve build time and performance.
3. Avoid Docker Security Vulnerabilities by Ditching Root Access
This one’s a biggie. Although Docker allows running containers as root by default, that doesn’t mean you should.
Why It’s Risky: If an attacker breaks into a container running as root, they might gain access to the host system.
So, Do This Instead:
- Use the
USERdirective in Dockerfiles to switch to non-root users. - Drop Linux capabilities using
--cap-drop. - Use tools like AppArmor or SELinux for extra control.
Quick Fix:
RUN adduser -D appuser
USER appuser
4. Turn on Docker Content Trust (DCT)
First off, let’s talk about integrity—because you definitely want to know your image hasn’t been tampered with, right? Next, Docker Content Trust (DCT) steps in to save the day by cryptographically signing every image. Consequently, any unsigned or altered image is instantly rejected. So, just set DOCKER_CONTENT_TRUST=1 before you pull or push, and voilà—you’ve locked down your supply chain.
That’s Where DCT Comes In:
- It verifies the digital signatures of Docker images.
- Just set
DOCKER_CONTENT_TRUST=1before pulling or pushing images.
Added Bonus: You’ll be alerted if the image is unsigned or compromised.
5. Secure Your Software Supply Chain
First off, imagine your supply chain as a long pipeline built on trust. However, if just one link goes weak, the whole thing can fall apart. Therefore, securing every step—from code to container—is now more important than ever.
Here’s How to Do It Right:
- First, generate SBOMs (Software Bill of Materials) so you always know exactly what’s inside your images.
- Next, use signed commits and tags in your repositories to ensure every change is tracked and trustworthy.
- At the end of the day, use private and verified registries — better safe than sorry when it comes to container images.
Recommended Tool: Syft by Anchore for generating SBOMs.
6. Scan Your Images — Always
Okay, now let’s get to vulnerability scanning. Even if you pick official images, they can still have outdated libraries. Therefore, you should integrate scanners like Trivy or Clair into your CI/CD pipelines. Next, automate scans after every image build so nothing slips through the cracks. Moreover, don’t just scan—review and remediate findings right away. Finally, schedule routine scans to catch newly discovered issues as they emerge.
So, What’s the Fix?
- First, integrate scanners like Trivy, Clair, or Snyk into your CI/CD pipelines so you catch issues early.
- Next, automate scans after every image build to ensure nothing slips through the cracks.
- Finally, act on the results right away—don’t just ignore them!
Popular Tool: Trivy — simple, fast, and free.
7. Isolate Containers with Network Segmentation
Containers talk to each other. That’s cool — until one gets infected and spreads malware.
To Stop This:
- First, create custom Docker networks instead of relying on the default bridge—this gives you more control from the get-go.
- Next, control which containers can communicate — no need to open up connections that aren’t really needed.
- Finally, use firewalls or service meshes for deeper control and tighter security.
Use Case: In a microservices app, isolate the payment service from everything else. Only the frontend and database should talk to it.
8. Protect Containers in Runtime
Building secure containers is just the beginning. What happens if something goes wrong during runtime?
You’ll Need:
- First, use real-time monitoring tools like Falco or Sysdig to keep an eye on container behavior.
- Next, set up alerts for any suspicious actions—think shell access or unexpected malware downloads.
- Finally, apply behavior-based rules so you can catch unknown threats before they cause damage.
Link: Falco by Sysdig
9. Don’t Store Secrets in Containers
This tip can’t be repeated enough. Secrets (API keys, tokens, passwords) don’t belong in your code or Dockerfile.
Best Practices:
- First, use Docker Secrets in Swarm or Kubernetes Secrets in K8s to keep your keys safe.
- Next, rotate those secrets regularly so old credentials can’t be exploited.
- Finally, consider external tools like HashiCorp Vault or AWS Secrets Manager for even stronger protection.
Don’t Do This:
ENV DB_PASSWORD=mysecret
10. Harden the Docker Host Itself
Let’s not forget the machine running all your containers. If it’s weak, everything else is at risk.
Security Tips:
- First, choose container-focused OSs like Bottlerocket or Talos—they’re built lean and secure just for Docker.
- Next, shut down any ports and services you don’t need so there are fewer doors for attackers.
- Finally, make sure the Docker socket (/var/run/docker.sock) is locked down — only trusted users or processes should have access to it.
Bonus: Use docker-bench-security to run automatic host security audits.
Click here to get more insight about: How to Pick the Best AWS Disaster Recovery Strategies
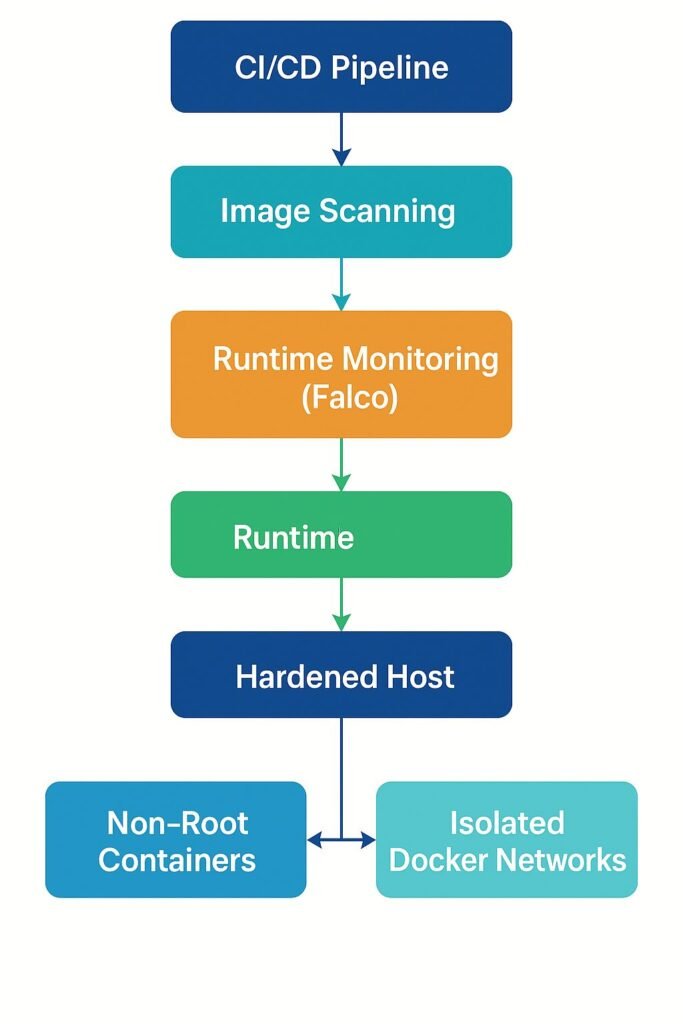
Architecture: Secure Docker Deployment
Conclusion: Docker Security Vulnerabilities
Let’s face it — Docker really does make things simpler. But if you ignore security, it can quickly turn into a nightmare. Thankfully, with the tips above, you can stay one step ahead. From using non-root users and scanning images to enforcing runtime protection and supply chain security — it’s all about being proactive.
So, go ahead. Review your Docker setup today. Fix what’s broken. Monitor what matters. And above all, don’t wait for an incident to learn these lessons the hard way.
Click here for more insights on various Cloud Computing || Automation || Cyber-Security
FAQs:
Q1: What’s the best way to prevent privilege escalation in Docker?
Answer: Well, first, run your containers as non-root users. Next, drop all unnecessary Linux capabilities. Moreover, enforce AppArmor or SELinux profiles to lock down system calls. Finally, keep your kernel and container runtime up to date to close any loopholes.
Q2: How do I make sure images from Docker Hub are safe?
Answer: To begin with, stick to official or verified images. Then, enable Docker Content Trust so you only pull signed artifacts. Furthermore, scan every image with tools like Trivy or Clair before deployment. Lastly, stay informed about image CVEs and updates.
Q3: Can runtime tools like Falco catch zero-day attacks?
Answer: At first glance, Falco’s behavior-based rules flag unusual container actions in real time. Meanwhile, it watches for unexpected system calls or file changes. Although it can’t catch every zero-day, it often spots novel threats early. So, it’s a great addition to your defense strategy.
Q4: How do I prevent secret leaks during container builds?
Answer: First of all, never bake secrets into Dockerfiles or ENV vars. Instead, use dedicated secret managers like Docker Secrets, Vault, or AWS Secrets Manager. On top of that, inject credentials at runtime only. Finally, always add .env files to .gitignore and rotate keys regularly.
For further reading and tools:

