Content:
- Introduction
- Understanding Advanced Persistent Threat APT
- Analysing Advanced Persistent Threats Intelligence
- The Anatomy of an Advanced Persistent Threats Attack
- Monitoring Incident Response Data
- Protecting Against Advanced Persistent Threats (APTs)
- Advanced Persistent Threats: Leveraging Automated Tools
- Applying a Proactive Mindset
- Incident Response and Recovery
- Collaborating with Industry Partners
- Real-World Example of APTs:
- Visualizing Emerging Tactics of Advanced Persistent Threats
- Overcoming the Challenges of APT Defence
- The Future of Advanced Persistent Threats Défense
- Conclusion: Advanced Persistent Threats (APTs)
- FAQs:
Introduction
As cybersecurity professionals and incident response teams, it is very much crucial to stay ahead of the latest threats. Equally important is understanding the tactics used by Advanced Persistent Threats (APTs) actors. This guide gives the information and devices to distinguish emerging strategies in Advanced Persistent Threat. Consequently, you can better protect your organization against these sophisticated attacks.
Understanding Advanced Persistent Threat APT
Advanced Persistent Threats (APTs) are a severe kind of cyberattack. These attacks are not just random; they target specific organizations or individuals. APTs are known for being persistent, sophisticated, and using tailored techniques. Often, they are state-sponsored and aim to infiltrate networks, steal sensitive data, or disrupt operations over a long time.
To effectively counter APTs, it’s crucial to understand their Tactics, Techniques, and Procedures (TTPs). We can spot new tactics by analyzing past APT incidents and staying informed about the latest trends. Consequently, we can develop proactive defence strategies. This knowledge helps us anticipate potential threats and respond more quickly. Additionally, continuous learning and adaptation are essential to staying ahead of APT actors.
In summary, APTs are a significant threat due to their targeted and persistent nature. Understanding and adapting to their tactics is critical to defending against these sophisticated attacks.
Analysing Advanced Persistent Threats Intelligence
One fundamental way to spot emerging APT tactics is through threat intelligence analysis. Moreover, this involves gathering data from security reports, industry blogs, and government alerts. Reviewing this data lets you identify patterns and new techniques APT groups use.
For example, a cybersecurity report might reveal a new phishing technique targeting financial sector employees. Such intelligence helps your team anticipate and defend against similar attacks. Staying updated with these reports allows you to refine security measures and share valuable information with your team.
The Anatomy of an Advanced Persistent Threats Attack
APT attacks often follow a predictable pattern called the “Cyber Kill Chain.” So, This process includes several steps: surveillance, weaponization, delivery, exploitation, installation, command and control, and data exfiltration. Attackers use various tactics like phishing and zero-day vulnerabilities. They might also exploit insider threats to infiltrate a target’s network. Consequently, they can maintain persistent access over a long time.
By recognizing these steps, you can better defend against APT attacks. Understanding how attackers operate helps you stay one step ahead and protect your organization effectively.
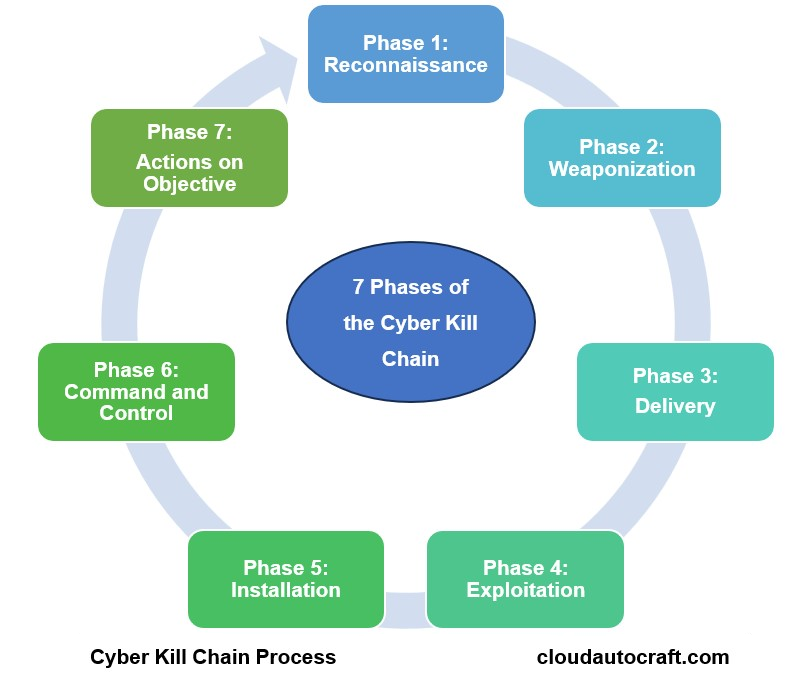
Click this below video to get more insight about Cyber Kill Chain :
Monitoring Incident Response Data
Another valuable way to spot emerging APT tactics is by analysing your incident response data. In fact, Look closely at past incidents to identify recurring patterns. Specifically, examine the attacker’s methods, entry points, and targeted data. Consequently, you may uncover new tactics.
For example, a spike in attempts to exploit a specific vulnerability is significant. Likewise, a sudden increase in a particular malware variant might indicate a new tactic used by an APT group. Sharing this information with your security team and industry peers helps build a collective understanding of the evolving threat landscape.
Protecting Against Advanced Persistent Threats (APTs)
Defending against APTs requires a multi-layered approach. Furthermore, We must combine advanced security technologies, robust incident response planning, and comprehensive employee training. Key strategies include:
| Threat Intelligence | Staying up-to-date on the latest APT trends, tactics, and indicators of compromise is crucial. So, This helps us better anticipate and prepare for potential attacks. |
| Network Monitoring | Implementing robust network monitoring and anomaly detection tools is essential. These tools help you identify and respond to suspicious activity in real-time. |
| Incident Response | Having a solid incident response plan is critical. It ensures your team knows what to do if an APT attack occurs, minimizing damage and recovery time. |
Click this below video to learn more about The Prevention of APTs:
Advanced Persistent Threats: Leveraging Automated Tools
In addition to manual analysis and collaboration, using automated tools to identify emerging APT tactics is highly beneficial. These tools can scan vast amounts of data, detect anomalies, and flag potential threats. As a result, your team can focus on the most critical issues.
For example, you could use a Security Information and Event Management (SIEM) system. This system aggregates and analyzes log data from across your organization. Moreover, it looks for indicators of compromise (IoCs) associated with known APT groups. You can quickly identify and respond to emerging threats by automating this process. Consequently, this reduces the risk of a successful attack.
Additionally, leveraging SIEM systems allows you to streamline threat detection and response. Furthermore, this proactive approach enhances your overall security posture.
Applying a Proactive Mindset
Identifying emerging APT tactics requires a proactive mindset and a commitment to continuous learning. It’s not enough to simply react to the latest threats. Instead, you must also anticipate and prepare for future tactics.
You also stay informed on industry trends and participate in training and professional development opportunities. Additionally, fostering a culture of innovation and risk-taking within your organization is essential. By embracing a proactive approach, you can better position your team to detect and respond to advanced persistent threats, even as they evolve.
Incident Response and Recovery
Even with robust security measures, we must be ready to respond effectively to APT incidents. Therefore, This means having a clear incident response plan. It outlines the steps to take if a breach occurs, including threat containment, evidence preservation, and data recovery.
Regular incident response drills and simulations are crucial. They ensure we can respond swiftly and effectively to an APT attack. This preparation is critical to minimizing damage and restoring normal operations quickly.
Collaborating with Industry Partners
Effective defence against APTs often requires working closely with industry peers and security organizations. By sharing information and best practices, we better understand the latest APT tactics. This collaboration helps us develop more robust defence strategies.
For example, participating in industry forums like the FIRST.org community is beneficial. Security professionals exchange insights on emerging threats and coordinate incident response efforts here. This proactive approach helps us avoid threats and enhances our organization’s security posture.
Real-World Example of APTs:
The OPM Data Breach
In 2015, the U.S. Office of Personnel Management (OPM) faced a significant data breach. It’s believed Chinese state-sponsored actors orchestrated it, accessing the personal details of millions of federal employees. However, This included sensitive data like security clearances and fingerprints.
This breach underscored the critical need for more robust cybersecurity measures. It also highlighted the necessity for more effective collaboration between government agencies and private sector organizations.
Dragonfly APT Group
One real-world example of identifying emerging APT tactics is the Dragonfly APT group, or Havex or Energetic Bear. This group has been active since 2011 and targets organizations in the energy, aviation, and critical infrastructure sectors.
In 2014, researchers at Symantec identified a new tactic used by Dragonfly. Specifically, it involved using a watering hole attack to infect victims. By compromising legitimate websites frequented by their targets, the group delivered malware and gained a foothold within the targeted organizations.
By closely monitoring and analyzing this incident, security teams were able to develop countermeasures. Consequently, they are more ready for comparative strategies that might be utilized by Dragonfly or other Able gatherings later on.
Visualizing Emerging Tactics of Advanced Persistent Threats
| Reconnaissance | APT actors often conduct extensive surveys to gather information about their targets. Consequently, this includes employee details, network architecture, and security controls. By identifying new techniques used for the study, you can better defend against initial access attempts. |
| Lateral Movement | Once inside the network, APT groups will use various techniques to move laterally. They aim to gain access to sensitive data or critical systems. Therefore, monitoring for emerging lateral movement tactics can help you detect and respond to these threats more effectively. |
| Data Exfiltration | The ultimate goal of many APT attacks is to steal valuable data, such as intellectual property and financial information. Identifying new methods for data exfiltration can enable you to better protect your organization’s sensitive information. |
Overcoming the Challenges of APT Defence
Defending against APTs is a complex and ongoing challenge for organizations like yours. Attackers continuously evolve their tactics and techniques, making it difficult for you to keep up. Consequently, some critical challenges you face include detecting and responding to stealthy, long-term intrusions. Additionally, it would help if you had specialized security expertise, which may be hard to come by.
Moreover, you often have limited resources and budgets. So, you can significantly reduce your risk by adopting a comprehensive and proactive approach to security. Finally, this enables you to protect your critical assets better.

The Future of Advanced Persistent Threats Défense
As the cybersecurity landscape evolves, so must our defences against APTs. Emerging technologies, such as artificial intelligence, machine learning, and quantum computing, can revolutionise how we detect, respond to, and mitigate these advanced threats. Additionally, increased collaboration between government, industry, and academia will be crucial in staying ahead of the curve and ensuring the long-term security and resilience of our critical systems and infrastructure.
Conclusion: Advanced Persistent Threats (APTs)
Advanced Persistent Threats (APTs) pose a significant and ongoing challenge for organizations like yours. They target government agencies, critical infrastructure, and other high-value targets. Therefore, understanding the nature of these threats and leveraging the latest security technologies and threat intelligence is crucial. By doing so, we can enhance our defences.
Moreover, fostering a culture of security awareness and collaboration is essential. This helps us better protect our most valuable assets. Furthermore, staying vigilant and maintaining a proactive, multi-layered approach to cybersecurity is key to success, especially in the face of these sophisticated and relentless attacks.
Click here to Read more about Cloud-Security – 2024 && DevOps-Security – 2024
FAQs:
What are the latest tactics being used by Advanced Persistent Threats (APTs)?
Answer: We constantly monitor APT activity to identify new tactics. Recent examples include fileless malware and cloud-based attacks. By staying informed and adapting our defences accordingly, we aim to stay ahead of evolving threats. Additionally, collaborating with industry peers helps share insights and best practices in APT defence.
How can organizations stay ahead of emerging APT tactics?
Answer: By staying informed and proactive, you can anticipate APT tactics. Regularly updating security measures and training your team is essential. Moreover, collaborating with industry peers helps share insights and best practices. This enables organizations to collectively enhance their defenses against APTs.
What are the most effective strategies for detecting and responding to new APT tactics?
Answer: Implementing robust monitoring tools allows us to detect unusual activity swiftly. Our incident response plan guarantees a quick and efficient reaction. Additionally, conducting post-incident reviews helps us learn and adapt our defences for future incidents. By continuously refining our approach, we strengthen our resilience against evolving APT tactics.
How can businesses prioritize their defenses against evolving APT threats?
Answer: By conducting risk assessments, we identify critical assets and potential vulnerabilities. This enables us to allocate resources effectively. Additionally, using a risk-based approach makes sure our defenses focus on the most critical threats to our organization. By prioritizing defences based on risk, we optimize our security posture against APT threats.
Originally posted 2024-06-13 15:19:09.


3 thoughts on “How to Counter New Advanced Persistent Threats Tactics”