Content
- Introduction
- Understanding of Serverless Security
- Serverless Security Apps on AWS: Key Points
- Best Practices for AWS Serverless Security Applications
- Adhere to Least Privilege Access for AWS Serverless Security:
- Secure Environment Variables:
- Implement Input Validation to maintain AWS Serverless Security:
- Use Managed Services:
- Secure API Endpoints:
- Enable Logging and Monitoring for AWS Serverless Security:
- Keep Dependencies Up-to-Date:
- Implement DDoS Protection:
- Conduct Regular Security Assessments:
- Develop an Incident Response Plan:
- AWS Lambda: Serverless Security with AWS Services
- Conclusion: Serverless Security on AWS
- FAQs:
Introduction
AWS Serverless architecture can truly transform how we build applications. It simplifies our work by allowing us to concentrate on coding rather than server management. But, with this ease come some security challenges. To keep your applications and data safe, following best practices for AWS serverless security is important. In this blog, we’ll dive into key practices to boost the security of your AWS serverless setups.
Understanding of Serverless Security
Serverless security in AWS is all about keeping your serverless applications safe, like those running on AWS Lambda. Begin using IAM roles with the least privilege principle to secure your functions. Next, the AWS Secrets Manager will manage sensitive data, and AWS CloudWatch and CloudTrail will monitor activity. Additionally, AWS WAF and AWS Shield should be used to protect against vulnerabilities and DDoS attacks.
Following these steps ensures your serverless applications stay secure while enjoying the advantages of the serverless model.
Serverless Security Apps on AWS: Key Points
Develop backup and recovery plans to safeguard your serverless apps and data against disruptions. It’s crucial to have strong backup and recovery strategies in place.
Identity and Access Management (IAM)
- Firstly, use AWS IAM to control who can access your Lambda functions and other AWS resources.
- Ensure that each Lambda function has its own IAM role and follows the principle of least privilege, thus giving only the access needed to perform tasks.
- Regularly review and update your IAM policies to meet your security needs.
Event-Driven Security
- Secure the entry points to your serverless applications triggered by events, such as API Gateway, SNS, or DynamoDB triggers.
- Moreover, strong input validation and sanitization should be implemented to prevent attacks like injections.
- Finally, monitor and audit the events that trigger your Lambda functions to spot any unusual or suspicious activities.
Data Protection
- First, sensitive information, like API keys and database credentials, can be stored securely using AWS Secrets Manager or AWS Systems Manager Parameter Store.
- Next, encrypt your data both at rest and in transit. You can use AWS-managed or customer-managed encryption keys for this purpose.
- Set strict access controls and permissions to ensure only authorized users can access your sensitive data.
Logging and Monitoring
- Use AWS CloudTrail to keep track of all API calls made to your AWS resources, including your Lambda functions.
- Furthermore, connect your serverless applications to AWS CloudWatch. Hence, This will help you monitor and analyze security-related events, like unauthorized access attempts or unusual function activity.
- To enhance your Lambda functions’ security and observability, use AWS Lambda Powertools, which offers features like structured logging and custom metrics.
Dependencies and Third-Party Libraries
- Regularly review and update your Lambda functions’ dependencies and third-party libraries to ensure they don’t have known vulnerabilities.
- Additionally, use tools like OWASP Dependency-Check or Snyk to scan your dependencies for security issues.
- Set up a process to keep your dependencies updated and secure.
Runtime Security
- Maintain a secure runtime environment for your Lambda functions by applying the latest security patches to the underlying operating system and runtime.
- Also, the Lambda execution environment can be configured securely by turning off unnecessary services or features.
- Consider using AWS Lambda Powertools or third-party runtime security tools to boost your Lambda functions’ security further.
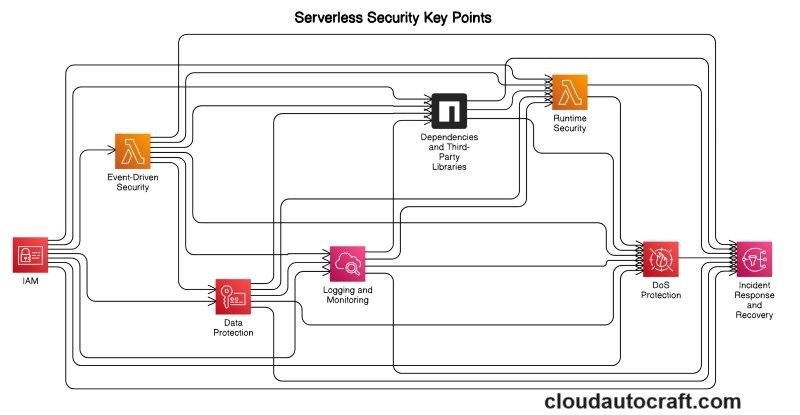
Denial of Service (DoS) Protection
- Utilize AWS Lambda’s scalability to help reduce the impact of Distributed Denial of Service (DDoS) attacks.
- Activate AWS Shield to defend your serverless applications from common DDoS attacks.
- Additionally, implement rate limiting and other protective measures to prevent your API endpoints from being overwhelmed.
Click here to get more insight about DDoS Attack on Kubernetes: What’s the Best Solutions
Incident Response and Recovery
- Create a thorough incident response plan for dealing with security issues, including containment, investigation, and recovery steps.
- Regularly test your incident response plan to ensure it’s effective and identify any areas needing improvement.
By following these steps, you will maintain strong security for your serverless applications, ensuring they run smoothly and safely.
Best Practices for AWS Serverless Security Applications
To keep your incident response plan up-to-date and effective, follow these tips:
Adhere to Least Privilege Access for AWS Serverless Security:
- Always follow the principle of least privilege when setting permissions for your Lambda functions.
- IAM policies restrict access to only the necessary AWS resources and actions to achieve this.
- Furthermore, it’s crucial to regularly review and update these IAM policies to ensure they remain aligned with your evolving security needs.
Secure Environment Variables:
- To keep sensitive information safe, securely store API keys or database credentials in AWS Secrets Manager or AWS Systems Manager Parameter Store.
- Instead of hardcoding this sensitive data directly into your Lambda function code, ensure it’s securely managed.
- Additionally, be sure that only authorized entities can access these stored secrets.
Implement Input Validation to maintain AWS Serverless Security:
- Validate all incoming data to keep your Lambda functions safe from threats like SQL injection or cross-site scripting (XSS).
- Next, AWS Lambda features like API Gateway or AWS WAF can be used to handle request validation and sanitization.
- Additionally, you can leverage tools like AWS Lambda Powertools for extra input validation and sanitization. This approach helps ensure your data remains secure and your functions run smoothly.
Use Managed Services:
- To securely store and manage sensitive data such as API keys or database credentials, utilize managed services like AWS Secrets Manager or AWS Key Vault.
- Additionally, to safeguard your serverless applications from web application vulnerabilities and DDoS attacks, employ managed security services like AWS WAF and AWS Shield. This way, you can ensure both your data and applications are well-protected.
Secure API Endpoints:
- To secure your serverless API endpoints, use API keys, OAuth, or JSON Web Tokens (JWT) for authentication and authorization.
- Additionally, implement rate limiting and other protective measures to prevent your endpoints from being overwhelmed.
- For effective management and security of your serverless APIs, consider using AWS API Gateway.
Enable Logging and Monitoring for AWS Serverless Security:
- To monitor your serverless applications, integrate them with AWS CloudWatch.
- Therefore, This lets you monitor and analyze security-related events, like unauthorized access attempts or unusual function invocations.
- Also, use AWS CloudTrail to log and track all API calls to your AWS resources, including your Lambda functions.
- To boost observability and security even further, consider using AWS Lambda Powertools. This combination helps you stay on top of any issues and secure your applications.
Keep Dependencies Up-to-Date:
- To keep your Lambda functions secure, regularly checking and updating their dependencies and third-party libraries is important. This practice helps avoid known vulnerabilities.
- Additionally, tools like OWASP DependencyCheck or Snyk can scan these dependencies for any security issues.
- Furthermore, implement a process to ensure your dependencies remain updated and secure. Following these steps can effectively protect your functions from potential threats.
Implement DDoS Protection:
- Take advantage of AWS Lambda’s scalability to lessen the impact of Distributed Denial of Service (DDoS) attacks.
- To further protect your serverless applications, enable AWS Shield to defend against common DDoS threats.
- Additionally, apply rate limiting or other defensive measures to keep your API endpoints from being overwhelmed. By using these strategies, you can effectively safeguard your applications..
Conduct Regular Security Assessments:
- To keep your serverless applications secure, perform regular security assessments, such as penetration testing or vulnerability scanning.
- However, This helps you spot and address potential weaknesses. Additionally, AWS-provided security services like AWS Security Hub or AWS Inspector can be used to automate and streamline the assessment process.
- Finally, make sure to address any identified vulnerabilities or security issues promptly. This approach ensures your applications remain secure and up-to-date.
Develop an Incident Response Plan:
- Create a clear incident response plan that outlines the steps to take during a security incident.
- Make sure the plan covers procedures for containment, investigation, and recovery.
- Additionally, the incident response plan should be regularly tested and updated to keep it effective and relevant. This approach helps ensure you are prepared to handle security incidents efficiently and minimize their impact.
By adopting these best practices and utilizing AWS’s security services, you can strengthen the security of your serverless applications and protect your data and systems from various threats.
Click here to get more insight about How to Ensure AWS S3 Bucket Security Best Practices
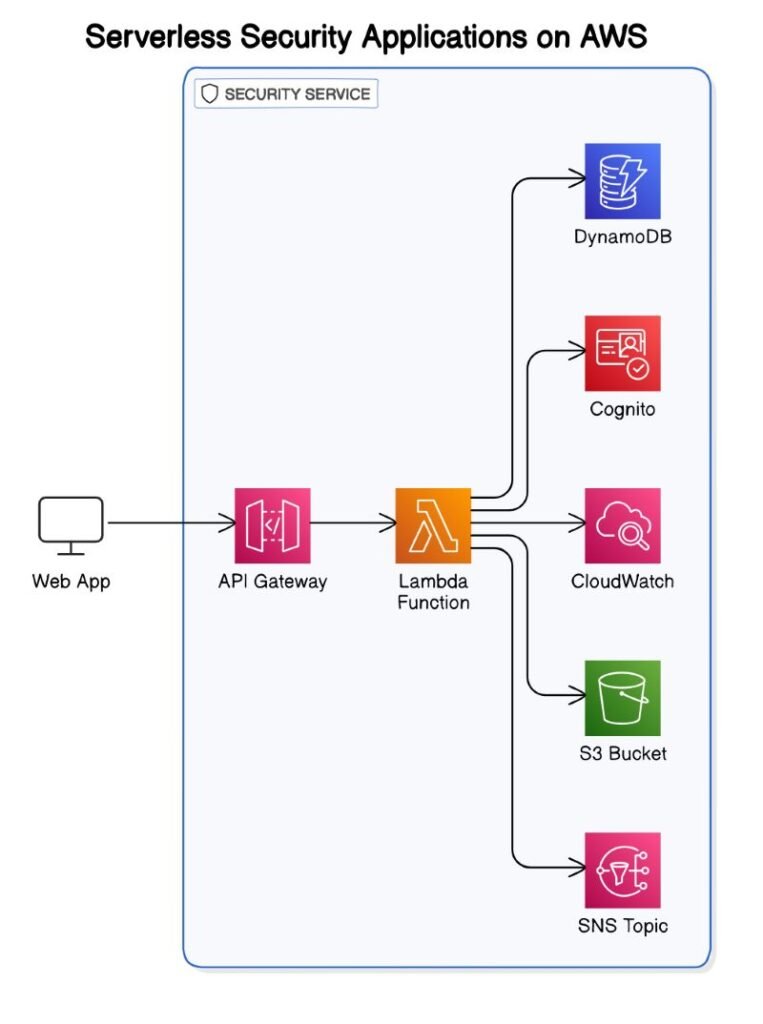
AWS Lambda: Serverless Security with AWS Services
Combining AWS Lambda with AWS security services is a smart strategy to keep your serverless applications secure. Lambda lets you run code without managing servers, and adding AWS security tools boosts your protection. Here’s a quick guide to enhancing your AWS serverless security:
- AWS Config: This service monitors and records changes to your AWS resources, including Lambda functions. It’s perfect for spotting unauthorized modifications and ensuring your resources stay secure.
- IAM (Identity and Access Management): Use IAM to manage who can access your Lambda functions and other AWS resources. Stick to the least privilege principle by creating specific IAM roles for your Lambda functions, which limits access to only what is necessary.
- CloudTrail: This service logs and monitors all API calls to your AWS resources, including Lambda, helping you track and investigate suspicious activity effectively.
- CloudWatch: Use CloudWatch to monitor your Lambda functions and set up alerts for security events, like unauthorized access attempts or unusual invocations. Therefore, This helps you respond quickly to potential threats.
- Lambda Powertools: Enhance your security and observability with utilities like structured logging, tracing, and custom metrics provided by Lambda Powertools.
- Secrets Manager: Securely store sensitive info like API keys or database credentials and rotate secrets regularly to reduce exposure risks.
- WAF (Web Application Firewall): Protect your serverless apps from vulnerabilities such as SQL injection and cross-site scripting (XSS) with AWS WAF.
- Shield: Shield offers automatic protection against Distributed Denial of Service (DDoS) attacks, ensuring your applications remain available and responsive.
By integrating these AWS services, you can greatly enhance the security of your serverless applications. Therefore, This approach fortifies your defences and ensures that your data and systems remain protected from various threats.
Conclusion: Serverless Security on AWS
Securing serverless applications requires a proactive and multi-layered approach. By implementing the best practices outlined in this blog post, you can significantly enhance the security of your serverless applications and safeguard your data and systems. Remember to stay vigilant, keep your knowledge and tools up-to-date, and continuously assess and improve your security measures.
With the right security strategies in place, you can fully harness the benefits of serverless computing while maintaining a robust and secure environment.
Click here to get more insight about DevOps-Security && Cyber Security
FAQs:
How do I protect sensitive data in AWS Lambda for Serverless Security?
Answer: Start by storing sensitive information in AWS Secrets Manager to keep your data safe. Then, all data will be encrypted at rest and in transit using AWS KMS. However, This helps minimize data exposure. It’s also important to implement least privilege permissions to limit access. Additionally, regularly review and rotate your secrets to reduce the risk of credential compromise. By following these steps, you can effectively enhance the security of your sensitive data.
How to ensure API Gateway security for Lambda for Serverless Security?
Answer: To ensure the security of your APIs, use API Gateway’s built-in authentication and authorization features. Always implement HTTPS to keep data secure during transit. Additionally, API throttling should be enabled to prevent abuse, and API caching should be implemented to improve performance. Continuously monitor API usage to detect any suspicious activity. By following these steps, you can enhance your APIs’ security and performance.
Why is secure deployment important for AWS Lambda functions?
Answer: Secure deployment is crucial for AWS Lambda functions as it prevents unauthorized access and protects sensitive data. You reduce vulnerabilities and mitigate risks by using encryption, the least privilege principle, and monitoring. Consequently, This ensures your applications remain secure and compliant, maintaining their integrity and safety from threats.
What are the best ways to monitor AWS serverless security?
Answer: Start by enabling AWS CloudTrail to track API calls, and then use AWS CloudWatch for detailed logging and monitoring. Additionally, leverage AWS Security Hub for a comprehensive security view and automate security tasks to streamline your processes. Furthermore, regular security assessments should be conducted to identify and address potential issues. Following these steps will ensure robust security and proactive management of your AWS environment.
Originally posted 2024-08-09 20:27:37.

